Software-Defined Vehicle
AutoCrypt TEE
Trusted execution environment for in-vehicle applications

Enhanced security platform for software-defined vehicles.
AutoCrypt® TEE is an ASPICE CL2-certified in-vehicle systems security solution dedicated to system-on-chip (SoC) platforms like Advanced Driver-Assistance Systems (ADAS), in-vehicle infotainment (IVI), and the central communication unit (CCU).
By establishing a trusted execution environment (TEE) within each application processor, AutoCrypt® TEE provides an isolated and secure platform of only trusted applications (TA), guaranteeing robust security.
Although hardware security modules (HSM) are highly effective at securing smaller units like MCUs and ECUs, the TEE is a more optimized and cost-effective approach to securing larger applications, ensuring compliance with UN R155 and ISO/SAE 21434.
How It Works
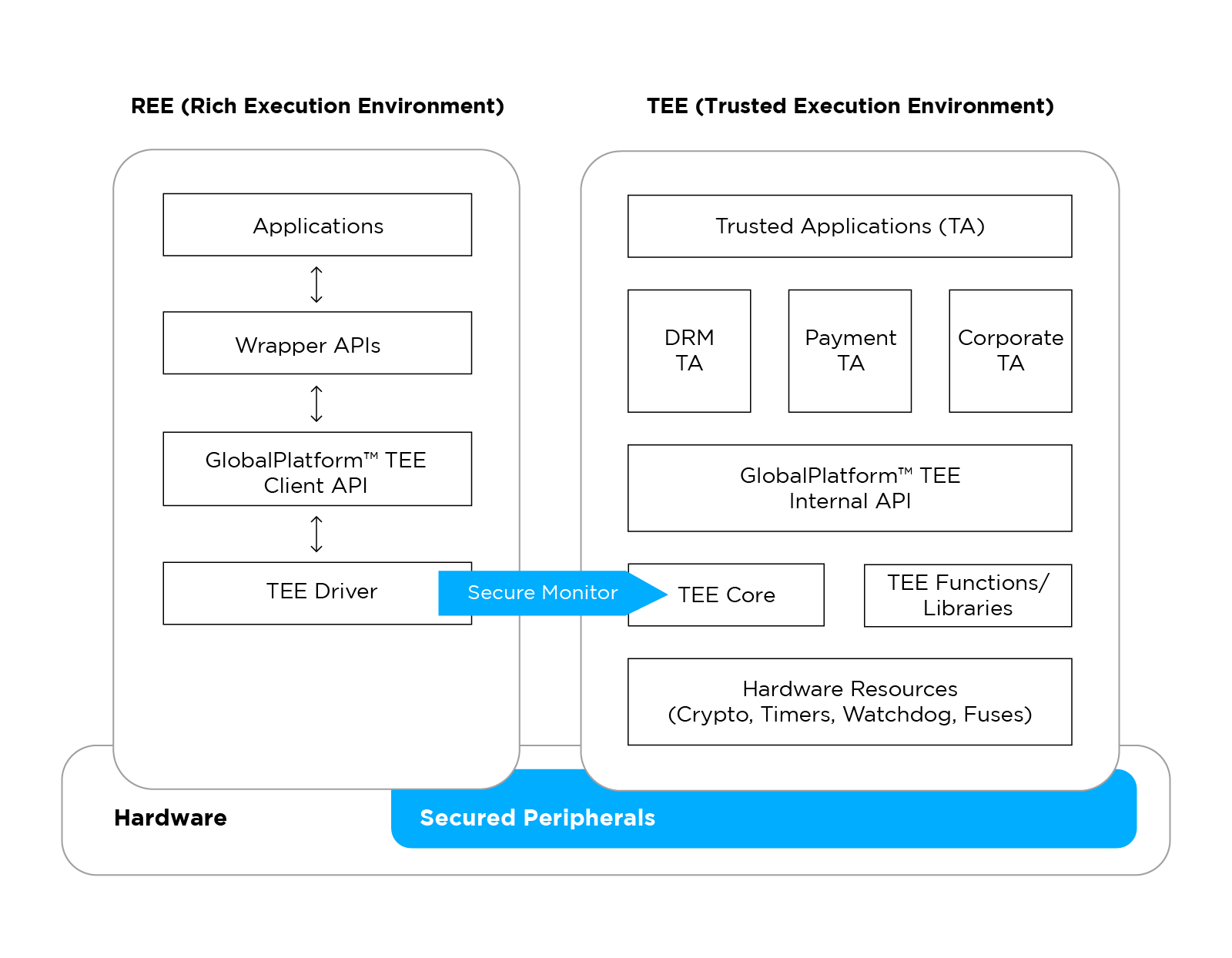
What Is a Trusted Execution Environment (TEE)?
A trusted execution environment (TEE) is an isolated environment for code execution, so that every application within the environment is safely protected from the rest of the device. All applications inside the TEE are called trusted applications (TA), each of them unable to access the data of other TAs.
The host environment on which a TEE is based on is called rich execution environment (REE). A TEE driver is built for applications in the REE, serving as a bridge to the TEE. TEE only allows the execution of code that has been validated and authorized.
Even if the REE of an application is compromised in an attack, the attacker would not be able to access the data within the TEE. The attacker cannot even manually copy any data in the TEE to other devices, as all data within the TEE are bound to the host device and will not run on any other devices.
Components and Features
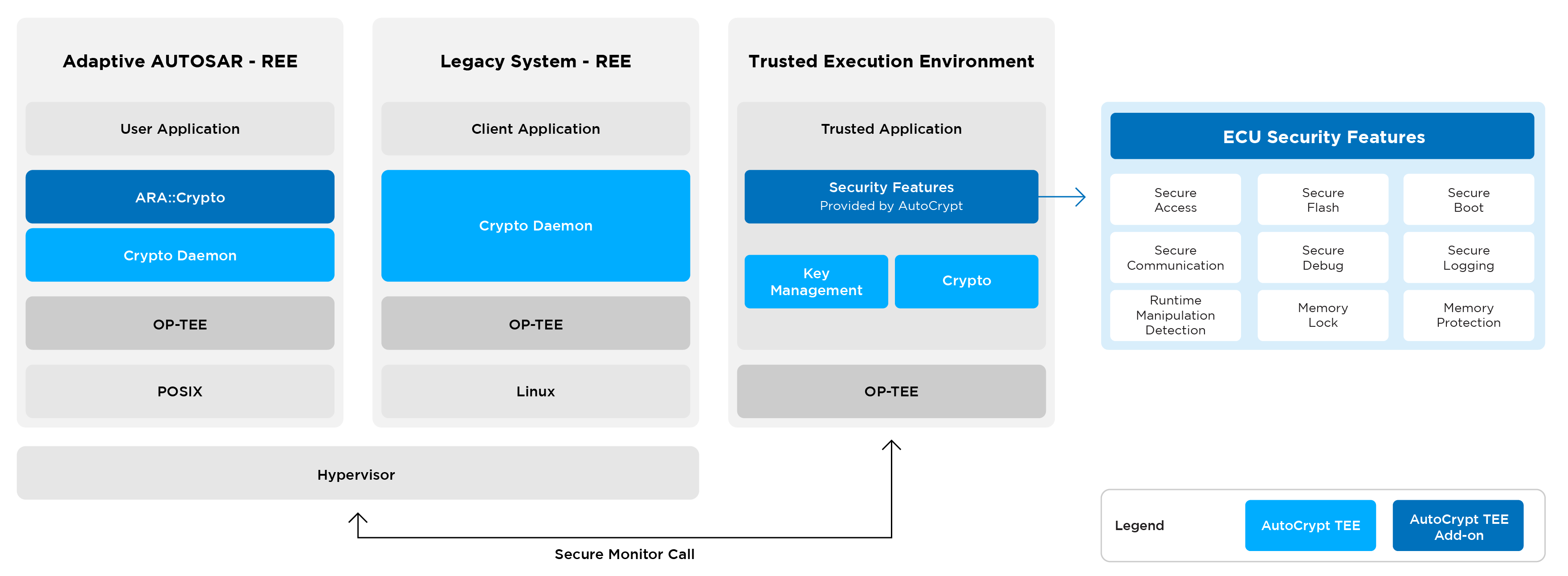
AutoCrypt TEE Components
AutoCrypt® TEE provides a secure TEE within each component of the application processor, enabling a more efficient, scalable, and upgradable approach to secure in-vehicle systems. Optimized for the vehicular software environment, AutoCrypt® TEE consists of:
- A crypto library that handles encryption and key management
- A crypto daemon that controls access and sends validated client requests to the trusted application (TA)
- A TEE application in charge of encryption, key management, and other security functions in the TEE
- All components needed for TEE implementation, including APIs, drivers, OS components, and a secure monitor, built in compliance with Adaptive AUTOSAR and GlobalPlatform™
Highlights
Adaptiveness and Compliance
- Compatible with Adaptive AUTOSAR R20-11
- Implementable in both AUTOSAR and legacy environments
- GlobalPlatform™ API compliance
- ASPICE-CL2 certified
- TrustZone for ARM-A technical specs supported
- MISRA-C/C++ validated
Add-On Security Packages
- Add-on security services available
- Connects to AutoCrypt® ASL, an add-on security cryptographer for easy implementation of Adaptive AUTOSAR
- Management and maintenance via OTA
Use Cases
Secure Boot
Guarantees software integrity by allowing the execution of only safe and verified software
Secure Flash
Protects sensitive data from unauthorized access by granting access to validated users only
Secure OTA
Ensures only validated packets are received and installed during OTA updates

CCU
Protects both the central communication unit and ECUs by two-way authentication
ADAS
Protects ADAS from malicious code execution by implementing robust access control
IVI
Protects personal data by encrypting them and keeping them in an isolated environment


