EV charging infrastructure sits at the center of the electric mobility transition. Yet according to the The HERE-SBD EV Index 2025, limited charging access remains the top barrier to EV adoption, with more than half of respondents (53%) citing a perceived lack of charging access as their primary concern.
Expanding the availability of charging stations is crucial, but so is securing the digital backbone that supports them. Public charging points are no longer simple power outlets, but digital infrastructures that handle sensitive information such as personal identifiers, payment credentials and vehicle contract certificates. Without robust safeguards, these data can become points of vulnerability, slowing adoption.
This blog explores three cornerstone frameworks shaping EV charging security — ISO 15118-2 (2014), the Open Charge Point Protocol (OCPP) 2.0.1 (2020), and the EU Cyber Resilience Act (CRA) (2023). By examining their roles and how they interconnect, we aim to simplify compliance in the EV charging ecosystem and highlight how integrators like AUTOCRYPT can help turn these standards and regulations into practice.
I. Interconnected Pillars of EV Charging Security
Securing EV charging infrastructure depends on three complementary pillars, each addressing a different layer of the ecosystem.
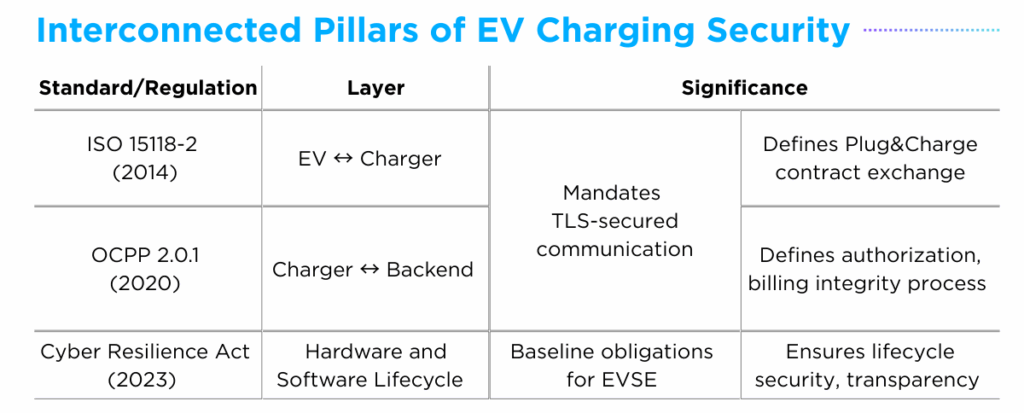
A) ISO 15118-2 (2014): Securing the EV, Charger Interface
The ISO 15118 multi-part standard (i.e. Part 1 – 2013, Part 2 – 2014, Part 3 – 2015, Part 20 – 2022) defines secure, interoperable communication between the vehicle and the charging station. While each part addresses different aspects of EV-EVSE interaction, Part 2: Network and application protocol requirements is especially significant as it lays out the technical implementation for managing secure communication flows.
ISO 15118-2 (2014) mandates that EV and EVSE establish a TLS-secured channel for direct current (DC) charging using certificate-based authentication. Within this secure channel, the Plug&Charge contract exchange is executed: the EV presents its contract certificate and the charger verifies it with the backend, enabling seamless authentication and billing. Later updates in ISO 15118-20 (2022) expand these provisions to cover both alternating current (AC) and direct current (DC) charging, as well as Vehicle-to-Grid (V2G) bidirectional energy flows.
Together, these measures ensure that the EV-charger handshake is both seamless and secure, protecting against spoofing and unauthorized access.
B) Open Charge Point Protocol (OCPP) 2.0.1 (2020): Securing the Charger, Backend Interface
The Open Charge Point Protocol (OCPP) 2.0.1 provides an open, interoperable standard for communication between charging stations and backend systems such as Charging Station Management System (CSMS) and mobility operators (MO).
OCPP 2.0.1 requires charging stations and backend systems to establish a TLS 1.2-secured channel with mutual authentication. Over this protected connection, OCPP defines operational protocols ranging from standardized message formats for anomaly reporting to the use of digitally signed meter values that ensure billing accuracy.
By embedding these measures, OCPP ensures chargers remain trusted, manageable and interoperable throughout their operational life.
C) Cyber Resilience Act (CRA) (2023): Hardware and Software Lifecycle
Although the Cyber Resilience Act (CRA) does not specifically target EV charging infrastructure, it strengthens EVSE security by covering hardware, firmware and backend systems under the category of “products with digital elements.”
Under the baseline obligations of the CRA, all EVSE must be secure at launch and throughout use, with manufacturers required to conduct conformity assessments before placing products on the market. Moreover, the CRA mandates secure update mechanisms such as OTA updates, vulnerability handling processes including coordinated disclosure, and obliges manufacturers to report actively exploited vulnerabilities.
In doing so, the CRA provides the regulatory umbrella that ensures ISO 15118 and OCPP implementations are maintained securely and transparently across both hardware and software layers.
Interconnected Security Chain
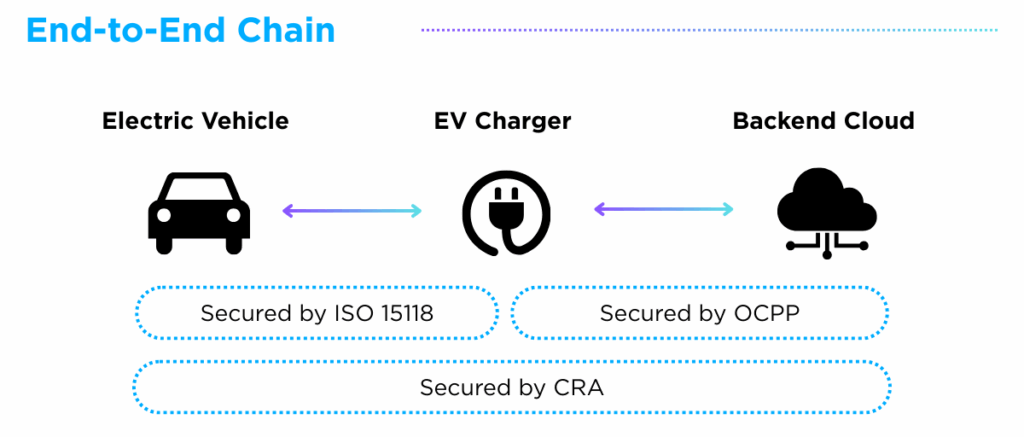
Viewed together, these three pillars create a security chain rather than isolated requirements. ISO 15118-2 secures the EV-charger interface, OCPP 2.0.1 governs charger-backend communications, and the EU Cyber Resilience Act sets mandatory cybersecurity obligations across hardware and software. Combined, they form an interconnected framework that strengthens resilience, ensures compliance, and builds trust throughout the entire EV charging ecosystem.
II. Autocrypt as the Integrator
AUTOCRYPT combines a deep understanding of standards-based requirements with practical expertise to deliver a wide range of solutions for securing EV charging infrastructure. By aligning with ISO 15118 and OCPP, and offering dedicated guidance on CRA compliance, AUTOCRYPT acts as an integrator that embeds end-to-end trust across the entire EV charging chain.
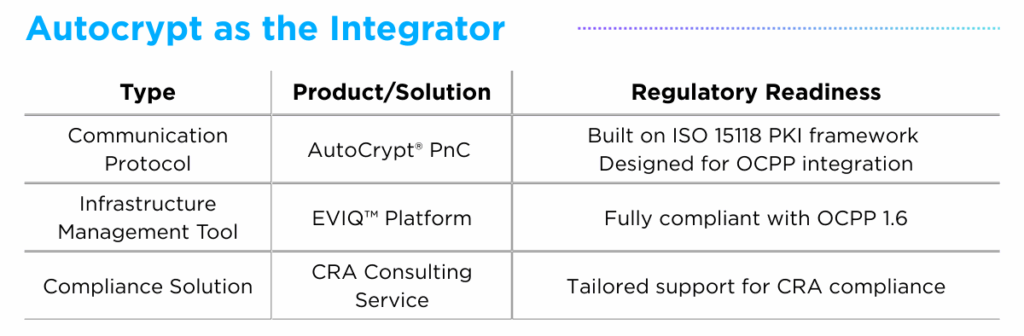
A) AutoCrypt® PnC
The AutoCrypt® PnC protocol incorporates mechanisms for both secure communication and PKI-based certificate management. Built on the ISO 15118 PKI authentication framework, it secures the vehicle-to-grid (V2G) communication interface through encryption and certificate-based trust. Moreover, designed for integration with OCPP, AutoCrypt PnC ensures contracts verified in the backend are securely delivered to the vehicle.
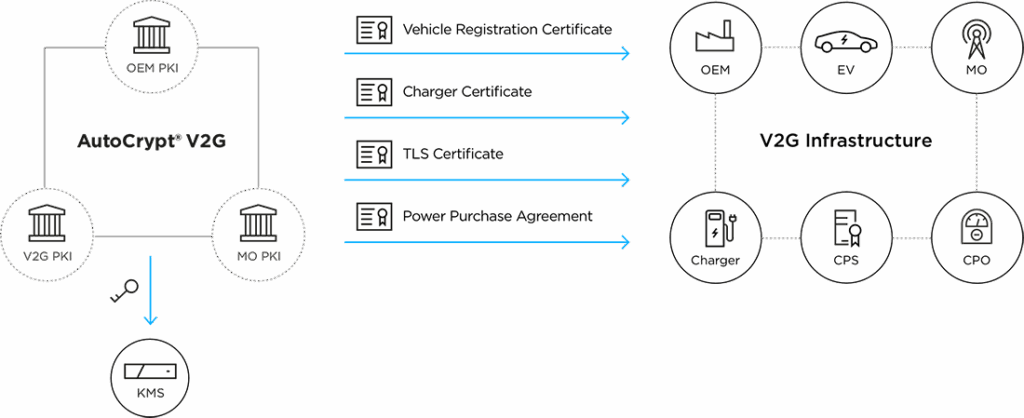
In doing so, it bridges front-end communication between the EV and charger with back-end contract flows, creating an unbroken chain of trust.
B) EVIQ™ Platform
Addressing the growing need for a unified and secure EV charging ecosystem, the EVIQ™ Platform combines applications, charger tools and management systems into one solution. Supporting Plug&Charge protocol outlined in ISO 15118 and fully compliant with OCPP 1.6, EVIQ provides both user-facing and operator-facing functions.
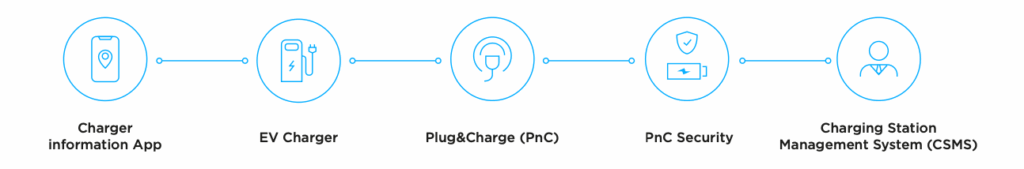
Together, these components make EVIQ a comprehensive platform which strengthens both user convenience and operator control.
C) CRA Consulting Service
With the EU Cyber Resilience Act (CRA) set for full enforcement in 2027, AUTOCRYPT’s CRA Consulting Service helps stakeholders systematically prepare for compliance. This includes support for OEMs, CPOs and mobility operators on security-by-design requirements, vulnerability management and update processes, compliance documentation.
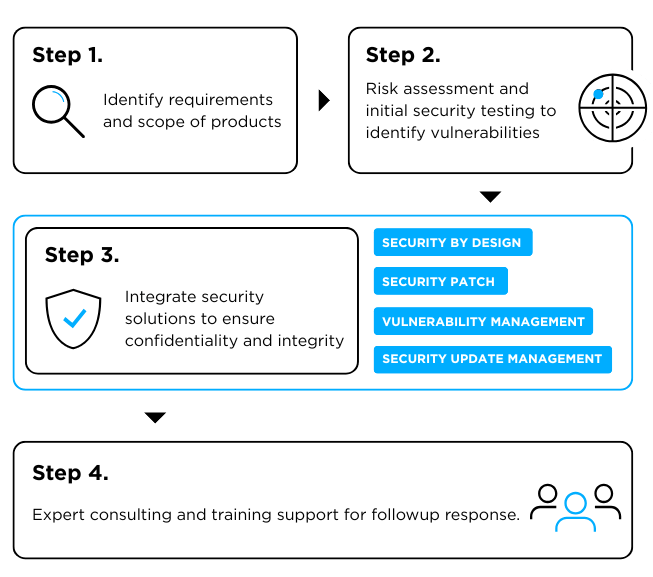
By guiding clients through each step, AUTOCRYPT ensures ISO 15118 and OCPP implementations are maintained securely and transparently, offering a clear pathway to regulatory readiness well ahead of the enforcement deadline.
III. Safeguarding the EV Charging Security Chain
The path to secure EV charging is not defined by a single standard or regulation, but by the interconnected security chain of ISO 15118, OCPP and the EU Cyber Resilience Act. Together, they safeguard the EV-charger handshake, protect the charger-backend connection, and ensure the long-term resilience of hardware and software systems.
AUTOCRYPT plays a pivotal role in uniting these layers. Through solutions such as AutoCrypt® PnC, EVIQ™ Platform and CRA Consulting Service, the company translates complex standards and regulatory requirements into practical, operational security across the charging ecosystem.
As EV adoption accelerates worldwide, AUTOCRYPT remains committed to building end-to-end trust and driving sustainable growth by continually expanding its suite of solutions for EVSE manufacturers, operators and mobility providers.
Learn more about our products and solutions at https://autocrypt.io/all-products-and-offerings/.