Autonomous driving presents the possibility of a future where individuals can engage in personal activities while traveling, without the need to focus on driving. Yet, questions remain as to whether such a future, free from manual vehicle control, will truly materialize. This blog introduces two distinct teleoperation methods designed to maximize the potential of safe autonomous driving.
The Spectrum of Autonomous Driving
As defined by SAE International, a global professional association of engineers in the automotive industry, automated driving systems are classified into six levels, ranging from Level 0 to 5.
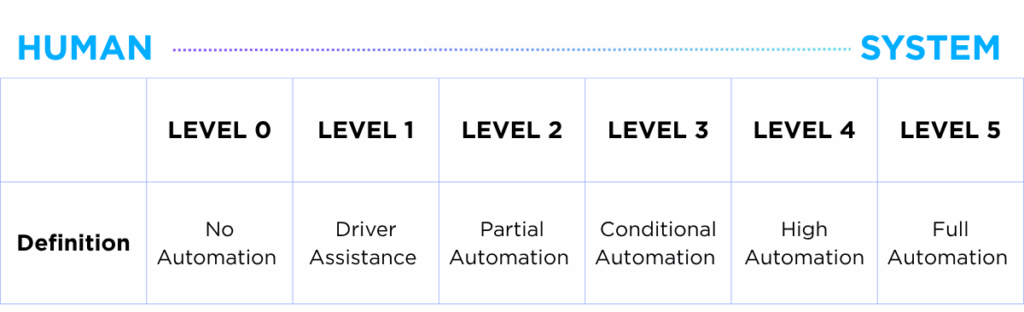
Level 0 represents full manual control, where the driver is entirely responsible for operating the vehicle, a scenario that reflects most current driving experiences. At this stage, no autonomous technology is applied.
For Levels 1 to 2, vehicles begin to assist the driver with features such as Smart Cruise Control, Lane Following Assist (LFA) and Autonomous Parking. From Level 3, autonomous driving becomes more pronounced, with conditional automation enabled under specific circumstances.
Level 4 marks a critical milestone in the advancement of autonomous driving. While it shares similarities with Level 3 in that the vehicle can autonomously steer the wheel, the key distinction lies in its ability to manage hazardous situations without human intervention. As such, Level 4 marks the stage where “full automation” starts to materialize.
Level 5 represents the highest level of vehicle autonomy, where a car can navigate across all environments without any restrictions on an ODD (Operational Design Domain), a set of defined conditions under which an autonomous system is designed to safely operate. At this stage, “full automation” is reached.
Most of the autonomous vehicles we see around us are currently positioned at Level 3. When a situation comes where AI (Artificial Intelligence) technology fails to respond, the driver needs to take command over vehicle operations and responsibility is bestowed upon the driver in case an accident arises. The maturity of autonomous technology becomes pivotal from Level 4 where the car must proactively respond to emergency situations in a safe manner without the interception of the driver.
Currently, autonomous vehicles are not yet resistant to object misdetection as they collect information through sensor devices such as cameras, radars, and LiDAR technology. Even if all sensors around the surrounding object are properly functioning, there may be instances where AI cannot fully comprehend an untrained scenario. In this case, human control becomes pivotal, whether it comes from the driver itself or from another subject. This is where teleoperation methods become relevant.
The Necessity of Teleoperations in Autonomous Driving
Imagine a typical scenario in which you are commuting home from work in an autonomous vehicle, using self-driving mode to catch up on delayed tasks. Suddenly, the vehicle encounters a situation where the conditions necessary for safe autonomous operations are no longer met. In other words, the system is unable to function properly, requiring the driver to assume control and take full responsibility. However, with the deadline approaching and the task still unfinished, the driver may choose to request teleoperation support. In such cases, a remote operator can assist in managing the situation without requiring the driver to take full control.
Teleoperation service can also be deployed in more extreme scenarios, such as during wartime or natural emergencies. This is unsurprising, given that the origins of teleoperation technology are rooted in military applications. As early as the 19th century, efforts were made to develop remotely controlled torpedoes, and the technology has continued to be explored for defense-related purposes ever since. One notable example is inventor Nikola Tesla’s 1898 demonstration of a remote-controlled torpedo—an ambitious attempt that, despite ending in failure, marked a pivotal moment in the history of teleoperation.

The use of teleoperation in military contexts is especially pivotal, as deploying personnel in active war zones can be extremely hazardous. In such cases, teleoperated vehicles or robots can be strategically positioned to reduce risk to human life. When factoring in the use of drones, teleoperation represents one of the most dynamic and rapidly evolving areas of military technology.
Teleoperation Control Modes in Autonomous Vehicles – Direct and Indirect
Teleoperations refer to the technology that enables communication and control between a vehicle and an external location, typically coordinated through a centralized control center. In essence, when an autonomous vehicle encounters an unexpected situation that its onboard AI cannot handle, a remote operator at the control center can intervene and take effective control of the vehicle on behalf of the user.
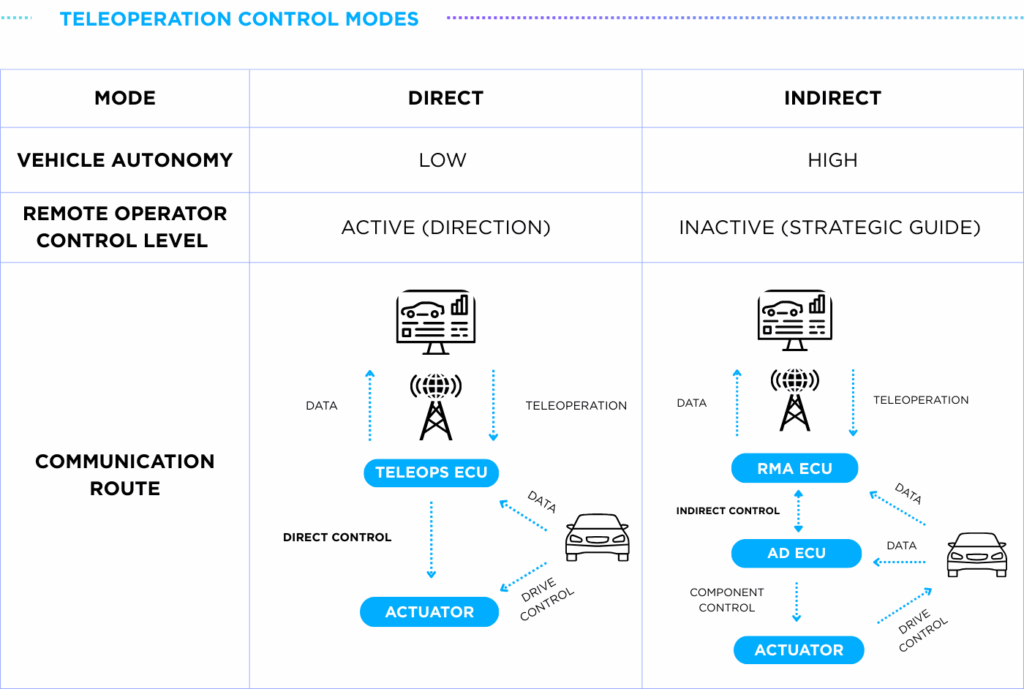
There are two main types of teleoperation control: direct and indirect, differentiated by the level of human involvement. In ‘direct teleoperation,’ a remote operator takes full, real-time manual control of the vehicle. In contrast, ‘indirect teleoperation’ involves shared control, where the vehicle retains partial autonomy while the operator provides high-level guidance.
Automakers have explored teleoperation as a solution for complex scenarios. For example, in December 2022, Hyundai Motors partnered with Israeli startup Ottopia to develop a teleoperation system called Remote Mobility Assistance (RMA), aimed at supporting Level 4 and higher autonomous driving instances. More recently, Tesla announced they were set to launch a limited robotaxi service in Austin, Texas, by the end of June 2025, heavily relying on teleoperators to assist in situations where the autonomous system encounters difficulties.
Direct Teleoperation Control
While teleoperation holds great promise, it also presents significant challenges, particularly when it comes to direct control. One major issue arises when there are network disruptions affecting data transmission, and information sent from the vehicle to the teleoperator gets delayed or not reflected in real time. Although rare, instances of network latency or unstable communication can cause a time lag in the control center’s response, potentially making it impossible to prevent an accident.
Moreover, an overreliance on direct teleoperation can be seen as an inefficient use of the advanced capabilities built into autonomous vehicles. Given that vehicles are already equipped with advanced sensors like LiDAR, radar and camera sensors for real-time decision-making, delegating control to a remote operator may underutilize these capabilities and limit the system’s full potential.
Indirect Teleoperation Control
Recognizing the limitations of direct teleoperation, current research highlights indirect teleoperation control as a more effective complementary solution.
As the term suggests, under indirect control, the teleoperator does not directly issue commands ranging from handle steering, acceleration, or braking. Instead, high-level or abstract commands are transmitted, while the vehicle itself executes detailed actions. This approach reduces dependence on constant network communication and allows the vehicle to make better use of its internal technologies.
A primary example of indirect teleoperation control in action is “navigational route assistance,” where drivers receive guidance from the vehicle on the most optimal path to reach a specific destination. Another use case is “recognition alerts,” where the system advises the vehicle on whether to detour or disregard certain road obstacles.
While direct teleoperation is always subject to the risk of unstable telecommunications, indirect teleoperation significantly reduces this vulnerability by making the vehicle less dependent on network connections. In this mode, the vehicle makes real-time decisions autonomously, with the teleoperator offering directional input rather than direct control. All onboard components and safety systems of the vehicle remain fully active and engaged, further reducing reliance on the control center operator.
Enabling safe autonomous driving through teleoperation control
It is expected that Level 4 autonomous vehicles will interchange modes between autonomous driving, direct teleoperation and indirect teleoperation. Although skepticism persists about when Level 5 autonomy will be fully achieved, advancements in the integration of internal and external communication systems continue to accelerate, bringing the future of save autonomous driving ever closer.
AUTOCRYPT stands as a leading automative cybersecurity provider with experience in facilitating remote driving assistance environments. In particular, AutoCrypt® RODAS (Remotely Operated Driving Assistance System) provides a failsafe for autonomous vehicles by giving authority for an authorized operator to take control over a vehicle when an unexpected situation arises. This can be done either remotely (i.e. teledriving) or through configuring driving policies based on the situation reported by the occupants (i.e. teleguidance).
To learn more about the Autocrypt’s teleoperation services, click here. Read our blog for more technology insights or subscribe to AUTOCRYPT’s monthly newsletter.