The Vehicle-to-Everything (V2X) ecosystem runs on a secure, decentralized certification system utilizing public key infrastructure (PKI) technology. Standardized as the Security Credential Management System (SCMS), the system ensures that every V2X end entity is given a unique set of digital certificates, generated and distributed by multiple layers of independent certification authorities (CA). These V2X end entities, including the onboard units (OBU) installed in vehicles and the roadside units (RSU) connected to points of road infrastructure, use their private key to sign off messages sealed with their certificates.
Such a PKI framework ensures trust in V2X communication by validating messages’ authenticity and integrity. “Authenticity” implies that the message’s sender is truly who they claim to be, while “integrity” signifies that the message has not been altered during transmission.
Message accuracy: the limitation of PKI
Although the PKI guarantees end-to-end security for all V2X communications, it does not exert control beyond the communication endpoints. Due to this limitation, the PKI is not capable of validating the content of messages, such as, whether the message contains accurate information about the vehicle and its environment. For instance, if a car is broadcasting a V2X message stating that it is traveling at 60 km/h while it is in fact traveling at 80 km/h, detecting this discrepancy is beyond the PKI’s capability. Given that vehicles rely on these V2X messages to make decisions on the road, it is crucial to ensure that all information is accurate.
There are a couple of potential reasons behind an inaccurate V2X message. The first involves a hacked vehicle. A malicious road user might hack into their vehicle to purposefully create false or misleading messages in order to cause changes in traffic in their favor. An external hacker could also do so to manipulate traffic. Although hacking into a vehicle is extremely difficult to accomplish given the sophisticated security measures, it does pose a potential risk to the V2X ecosystem.
Another factor there could lead to an inaccurate message is that a vehicle’s internal systems might be experiencing a malfunction that results in incorrect signals given to its OBU. Although no malicious actions are involved, it is still considered misbehavior and poses a threat to its surrounding environment.
The need for misbehavior detection for V2X
To minimize the risk of false messages, a misbehavior detection mechanism needs to be implemented in the SCMS ecosystem so that potentially malicious users can be removed from the V2X ecosystem immediately.
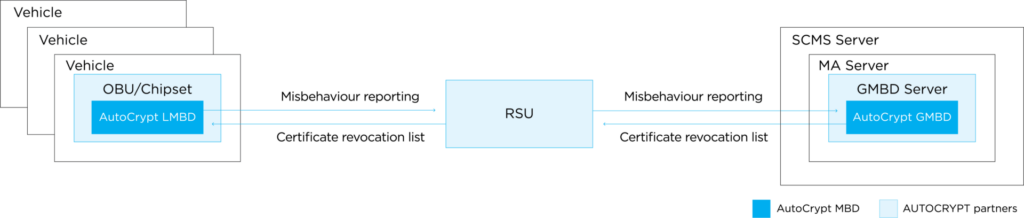
How is this done? AUTOCRYPT’s misbehavior detection solution, AutoCrypt® MBD, is deployed in both the end entity and the PKI server. The LMBD (local MBD) is embedded in the OBUs, screening all incoming messages for anomalies. The GMBD (global MBD), situated in the SCMS server, receives the list of flagged certificates from the LMBD, allowing the misbehavior authority (MA) to review and revoke the respective certificates. Once a certificate is revoked, it is added to the certificate revocation list (CRL) and distributed back to the LMBD so that the certificate is no longer recognized in the V2X ecosystem.
Although there has been no universal standard or agreement on what constitutes misbehavior, some common signs of misbehavior include:
- Attempting to use expired or invalid certificates
- Mismatched signature (private key)
- Unintelligible data (time, location, speed, et cetera)
AutoCrypt® MBD periodically updates its list of misbehaviors to address the latest threats, adding a final layer of security for the V2X ecosystem.
To learn more about AUTOCRYPT’s secure V2X solutions and services for C-ITS, check out Secure V2X Communications.



