
Enabling secure V2X communication for vehicles and infrastructure.
V2X (vehicle-to-everything) refers to the wireless technology that enables both direct and indirect communications from vehicles to vehicles (V2V), from vehicles to infrastructure (V2I), and from vehicles to pedestrians (V2P). V2X is the fundamental technology for Cooperative Intelligent Transport Systems (C-ITS) and a crucial enabler for safer and smarter autonomous driving (L3 and above).
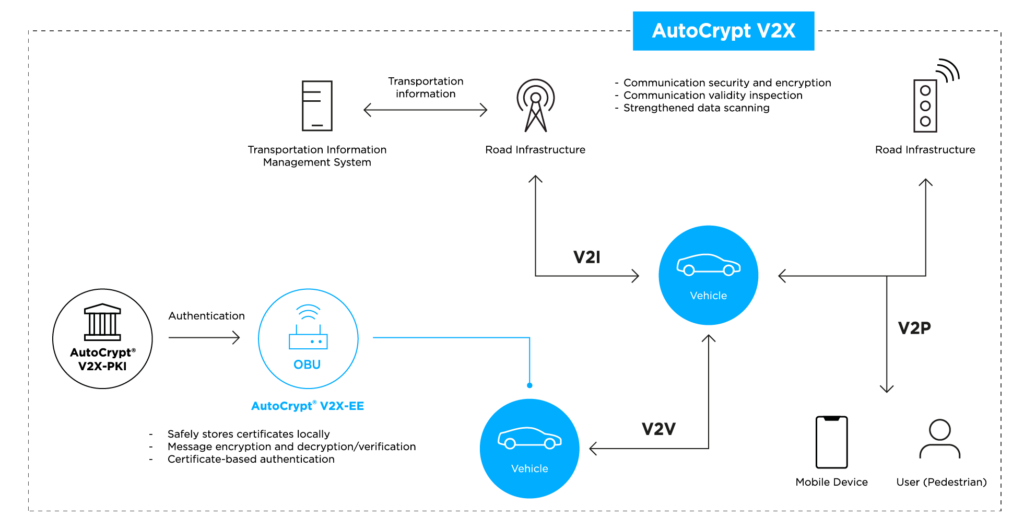
AutoCrypt® V2X-EE consists of an SDK (software development kit) that can be embedded into the V2X end entities in vehicles (onboard units) and points of infrastructure (roadside units), ensuring that messages transmitted between these participants are safely encrypted and two-way authenticated. This is done by enabling each V2X end entity to enroll and participate in the backend public key infrastructure. (see AutoCrypt® V2X-PKI)
How It Works
Encryption and digital signature: Securing the messages transmitted between OBUs and RSUs
AutoCrypt® V2X-EE is deployed as a software security module, embedded into the chipsets of V2X devices (OBUs and RSUs). It contains the security protocol and algorithms that enable the host device to participate in the V2X PKI — standardized as the Security Credential Management System, or SCMS — the authentication backend for V2X communications. This allows the host device to sign and encrypt outgoing messages and verify and validate incoming messages.
It also carries a local certificate manager (LCM), which stores and manages all certificates verified and signed within the V2X PKI (SCMS) ecosystem. This greatly reduces the computation load of the local unit and enables faster message transmission.
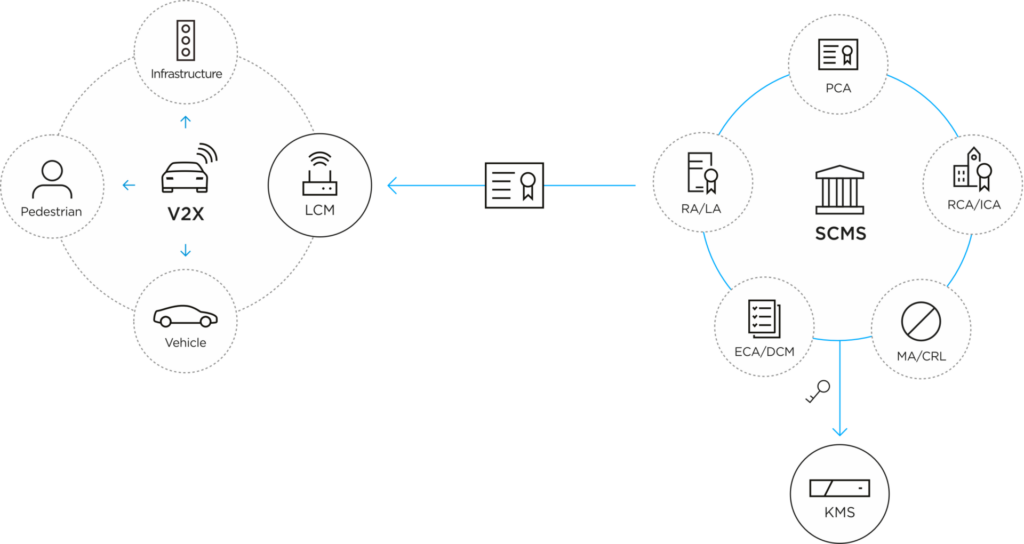
In the backend, AutoCrypt® V2X-PKI provides a tri-standard SCMS platform to enable certificate issuance, distribution, and revocation, completing the complete secure V2X communication process. (see AutoCrypt® V2X-PKI)
Highlights
AutoCrypt V2X-EE, core technologies
Learn how AUTOCRYPT’s technologies can advance vehicle security and ensure data integrity.

Encryption Library
Provides the necessary forms, protocols, and algorithms for communication encryption
Supports a wide range of hardware security modules

Security Module
Validates both sent and received messages by utilizing the encryption library
Extremely fast data throughput

Local Certificate Manager
Verifies the validity of digital signatures and stores them locally
Easily manages a great number of certificates

