Cybersecurity is one of the most complex and dynamic fields in the data-driven world, involving a constant battle between hackers and defenders. As internet connectivity reaches every corner of our lives, cybersecurity is now an essential component for automobiles. Yet, many are surprised to find out that cybersecurity in the automotive industry is entirely different from what we are used to encountering in the IT industry, and this means that there are challenges in terms of preparation and prevention. This article takes a closer look at how automotive cybersecurity differs from traditional IT security, with cybersecurity challenges unforeseen in the automotive industry.
1. Massive Scale and Density
As vehicles become increasingly digitalized and connected, many like to draw comparisons between cars and computers, referring to automobiles as “computers on wheels”. However, comparing a car to a computer is not quite fair because a car is, in fact, made up of hundreds of individual computers, which by industry terms are called electronic control units (ECU). The scale of the IT infrastructure in a vehicle resembles that of a small enterprise network, with all the computers, servers, and networking devices densely packed into this metal box. Now imagine having to manage cybersecurity risks for tens of millions of these densely packed “enterprise networks”; a single world-class OEM has between 20 to 100 million active vehicles on the road, a scale never seen in a single corporate IT environment.
Despite this seemingly impossible task, OEMs make cybersecurity scalable by incorporating it into the design and manufacturing stage. Since all vehicles of the same model contain an entirely identical IT infrastructure, they are able to pre-establish cybersecurity measures and embed them into the vehicle parts during the manufacturing stage. This brings us to the next point: type approval.
2. Regulations Requiring Cybersecurity Type Approval
In the IT industry, computer and device manufacturers are not directly responsible for the cybersecurity of their products. It is up to the users, mostly enterprises, to implement cybersecurity tools to protect their network and data. As a result, IT cybersecurity regulations tend to be enforced on enterprise users, not manufacturers. For instance, data privacy laws such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) mandate enterprises to have reasonable security measures to protect the customer data they possess. It is only recently that governments have started to require more transparent reporting from hardware manufacturers due to the latest surge of supply chain attacks.
In contrast, in the automotive industry, since cybersecurity must be deployed during the manufacturing stage, OEMs are directly held accountable for failures in cybersecurity implementation. UNECE’s WP.29 working party was the first to establish a set of regulations that require vehicular cybersecurity type approval, meaning that all vehicles must be assessed and qualified prior to being put on sale. The following diagram illustrates a stage-by-stage comparison of when cybersecurity is implemented between the automotive and the IT industry.
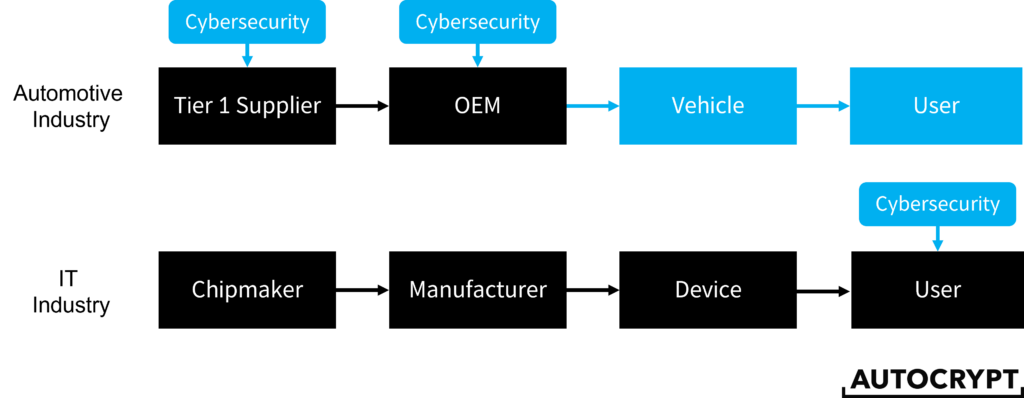
3. System Complexity
Besides having greater scale and density, the internal system of a vehicle—referred to as the E/E (electrical and electronic) architecture—is much more complex than that of a computer. With more than 30,000 hardware components moderated by over 100 ECUs, a single vehicle operates on over 100 million lines of code. What makes things more complex is that the in-vehicle system is largely distributed without a universal operating system; as each ECU serves a unique purpose, every one of them is crucial to a car’s functionality. For instance, some ECUs are paired with sensors and actuators. Some are paired with the powertrain. The ECU that provides wireless connectivity is called the telematics control unit (TCU)—or on-board unit (OBU)—overseeing communications between the vehicle and the outside world.
Given that the ECUs are highly sophisticated minicomputers, they are often manufactured by different third-party suppliers that specialize in their own field of expertise. This means that to implement cybersecurity throughout the vehicle, OEMs need to work with both cybersecurity providers and ECU manufacturers to ensure that all needs are aligned and all components interoperable. An example of such multi-party collaboration is demonstrated when AUTOCRYPT partnered with ECU manufacturer NXP Semiconductors to embed its AutoCrypt V2X software development kit (SDK) into NXP’s OBUs. The secured chipsets are then able to be delivered to OEMs for assembly.
As vehicles become more and more sophisticated, the industry is now looking for ways to group the ECUs by their domains of service and slowly work towards a more centralized vehicle system that is easier to assemble and manage, transforming the multi-tier supply chain into a more horizontal supply line.
4. Long Lifespan
Having covered the differences in the manufacturing process, it is now time to look at how car consumers differ from electronics consumers. With increasingly efficient engines, advanced mechanics, and precise quality control systems, vehicles now last longer than ever. As a result, more and more consumers are keeping their cars for longer, with the average age of vehicles on US roads reaching a record 12.1 years in 2020. This is three times the average age of computers in the US.
This might be good news to the consumers. Yet, long-lasting cars pose a new challenge to OEMs as they need to spend more effort into managing software updates for each car model to ensure that they are free of security vulnerabilities. More active vehicles on the road also put more strain on the Vehicle Security Operation Center (vSOC), which needs to constantly monitor all vehicle systems in real-time.
5. Scattered Locations
Speaking of vehicle monitoring, we need to talk about the unique challenges that the vSOC faces as compared to the SOC of an enterprise network. The computers and servers in a company do not move, hence it is easy for the cybersecurity team to monitor suspicious activities at all times and respond to threats immediately. On the other hand, vehicles move around constantly across cities and even countries. Oftentimes, they will enter zones without internet connectivity, making it difficult for the vSOC to detect and respond to threats due to delays in data transfer.
6. Damage Severity and Recovery
Lastly, in case a cyberattack happens, an enterprise will most likely lose sensitive data and experience operation disruptions. However, a successful cyberattack against a vehicle system not only puts data at risk, but the personal safety of the passengers and all those others on the road. Patching vulnerabilities is also more complex in the automotive industry because the OEM needs to work with different Tier 1 suppliers and cybersecurity providers to ensure smooth updates.
How AUTOCRYPT Overcomes Automotive Cybersecurity Challenges
What sets AUTOCRYPT apart from other automotive cybersecurity providers is its capability to offer a complete set of end-to-end solutions that help OEMs overcome all aspects of cybersecurity challenges throughout the vehicle. From securing in-vehicle systems and V2X communications, to EV charging and fleet management, AUTOCRYPT eliminates the complexity of searching for a different provider for each problem, making it a completely personalized experience for each client.
To learn more about AUTOCRYPT’s end-to-end solutions, contact global@autocrypt.io.
To stay informed with the latest news on mobility tech and automotive cybersecurity, subscribe to AUTOCRYPT’s monthly newsletter.



