In recent years, the automotive sector has undergone a profound transformation driven by innovation. The past decade witnessed a rapid digitization of vehicles, the ascent of electric powertrains, the advent of software-defined systems, and the ongoing development of autonomous vehicles. These technological advancements have elevated automobiles beyond mere modes of transportation. However, they also made vehicles increasingly susceptible to cyberattacks. Unfortunately, the pace of implementing in-vehicle cybersecurity measures has lagged behind the speed of innovation, leaving modern vehicles at an alarming risk.
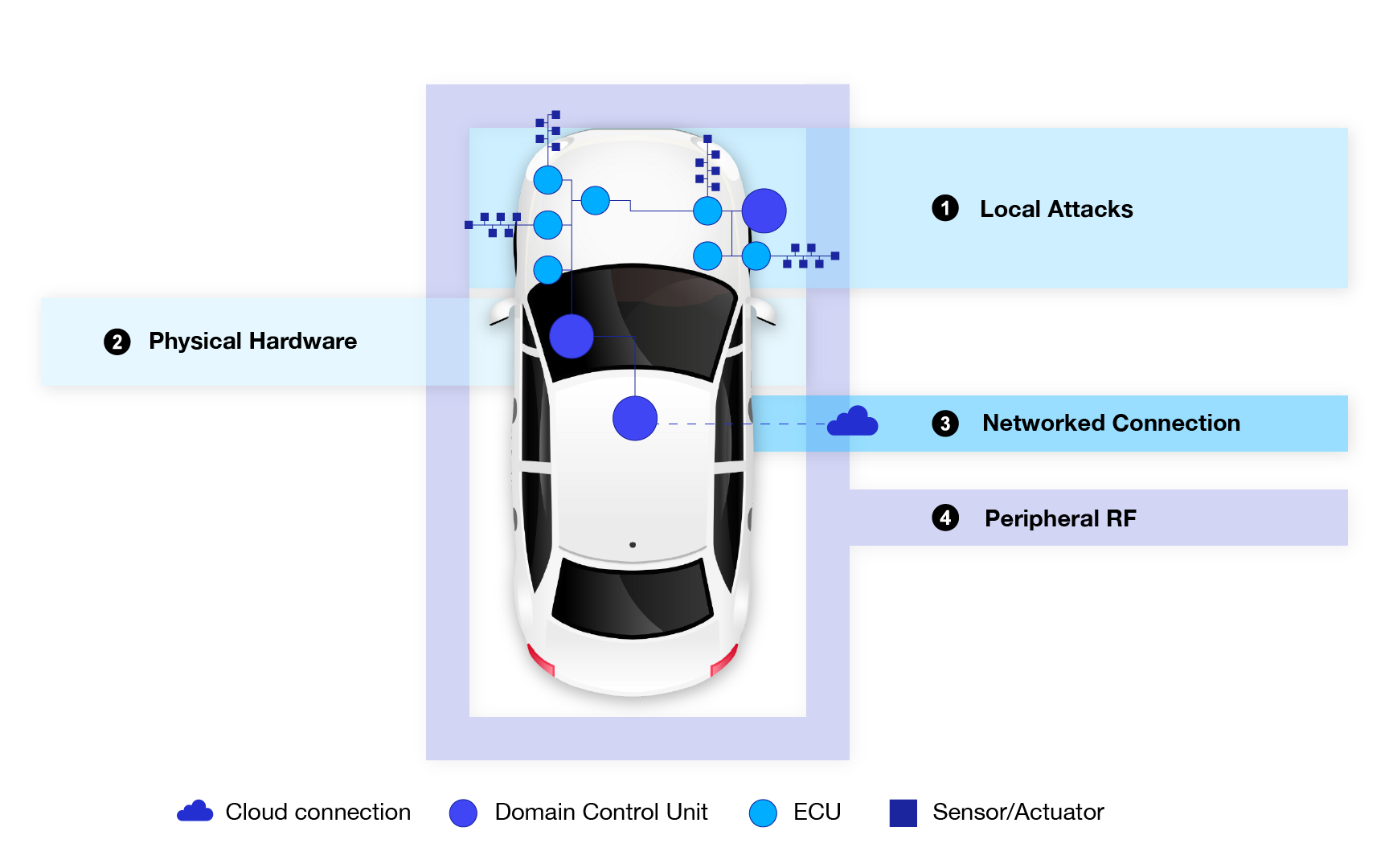
A comprehensive study conducted by IOActive has meticulously analyzed the trends in vehicle vulnerabilities, pooling data from 2016 to 2022. This study sheds light on the evolving threat landscape within the automotive industry, classifying data according to various attack vectors, namely local, physical, network, and peripheral RF.
Key Findings:
Networked Connection Attacks: The most striking revelation from the study is the surge in attacks exploiting networked connections, accounting for nearly half of all attacks in 2022. This signifies a prominent shift towards remote cyberattacks targeting vehicles.
Local Attacks: Local vehicle software, including operating systems, Electronic Control Units (ECUs), and Software Bill of Materials (SBOMs), accounted for 40% of disclosed vulnerabilities. This highlights the growing risk of exploiting vulnerabilities within a vehicle’s software ecosystem.
Physical Hardware Attacks: Physical hardware-associated vulnerabilities witnessed a significant decline, plummeting by 15%. This decline can be attributed to the automotive industry’s increasing focus on remote attack vectors.
Peripheral RF Attacks: Intriguingly, a novel category of attack vectors, peripheral RF attacks, emerged, representing 1% of the total vulnerabilities. This indicates the shifting landscape of vehicle cybersecurity needs and the expanding spectrum of threats.

Now, let’s delve into a closer examination of each attack vector:
Local Attacks
Local attacks primarily exploit vulnerabilities within the vehicle’s software ecosystem. Examples include attacks on operating systems, ECUs, and SBOMs. A common local attack is spoofing, where malicious actors send synthetic signals to deceive the vehicle’s systems. Spoofing can lead to incorrect data interpretation, posing substantial risks to vehicle operation and passenger safety.
Over the past decade, local attacks have seen a 6% increase, reflecting the industry’s struggle to defend against software-based attacks, exacerbated by the increasing complexity of software in modern vehicles. Robust in-vehicle security systems are essential to mitigating the risks of local software attacks. Manufacturers must employ effective testing measures to identify and rectify software vulnerabilities.
Physical Hardware Attacks
While physical hardware attacks have experienced a notable decline, they continue to pose a tangible threat. These attacks necessitate the physical presence of a threat agent. An attack on vehicle hardware could provide unauthorized access to critical vehicle components, potentially allowing a takeover of the vehicle.
For instance, a USB attack targeting a vehicle’s infotainment system could compromise the Controller Area Network (CAN). To address these vulnerabilities, vehicle security systems must incorporate robust gateway security measures to protect against hardware-based intrusions.
Networked Connection Attacks
Emerging as a recent development, networked connection attacks exploit far-field RF spectrum, including wireless and cellular connections, backend networks, and vehicle-to-everything communications. Securing messages exchanged through vehicle-to-everything (V2X) communication channels is of paramount importance, particularly as the industry is gearing up for autonomous driving. Ensuring the authenticity of V2X messages is crucial to prevent masquerading attacks, which can disrupt traffic and compromise vehicle systems.
Original equipment manufacturers (OEMs) must implement cybersecurity practices that authenticate information and signals exchanged through V2X communications to mitigate the risks associated with networked connection attacks.
Peripheral RF Attacks
Peripheral RF attacks originate in the near-field RF spectrum, encompassing technologies like NFC, RFID, remote key entry, and on-board telematics. The 1% growth in peripheral RF attacks, as identified by IOActive’s analysis, is largely attributed to vulnerabilities related to Remote Key Entry (RKE) and Bluetooth.
One common manifestation of a peripheral RF attack is a relay attack, notably compromising key fob technology. Such attacks can allow unauthorized access to vehicles and even the ability to remotely start them. These attacks have become one of the most common causes of vehicle theft. In 2022, AUTOCRYPT’s Vehicle Threat Research Lab discovered a high severity (CVSS 8.1) relay attack vulnerability (CVE-2022-38766) in a popular electric vehicle in Europe. To counter these threats, vehicle owners can employ signal-blocking devices, while manufacturers should implement comprehensive cybersecurity measures to monitor and filter traffic at the gateway.
In light of these evolving trends and vulnerabilities, it is imperative that advancements in the automotive sector go hand in hand with the development of robust cybersecurity measures.
AUTOCRYPT offers end-to-end vehicle cybersecurity solutions that safeguard vehicles from both internal and external threats, ensuring the continued safety and security of modern automobiles.
![[AUTOCRYPT] CES 2026 Highlights](https://autocrypt.io/wp-content/uploads/2026/01/12_8-D-30_2-est-2.png)



