Vehicular cybersecurity is now an inseparable component of automobiles. To establish an ecosystem where vehicles can safely connect with the outside world, UNECE’s WP.29 regulations on vehicular cybersecurity require automakers (OEMs) to manage cybersecurity risks at every stage of a vehicle’s lifecycle. This includes 1) pre-production design and development stage, where cybersecurity gets embedded into the supply chain; 2) production stage, where hardware and software components are integrated and tested for interoperability; and 3) post-production stage, where continuous monitoring and timely updates are required to keep the vehicle protected throughout its lifespan.
As a cybersecurity adviser on the International Transport Forum’s Corporate Partnership Board (CPB), AUTOCRYPT has been contributing its expertise in vehicular cybersecurity standardization and policymaking, making the company a specialist in cybersecurity integration and regulatory compliance. Developed to help OEMs integrate cybersecurity with functional safety, AUTOCRYPT’s in-vehicle security solution, AutoCrypt IVS, provides a robust end-to-end security package for all three stages of vehicle production, stretching beyond regulatory requirements.
In this article, we break down AUTOCRYPT’s in-vehicle security process to look at how a vehicle is secured at each stage.
1. Threat Assessment and Remediation Analysis (TARA)
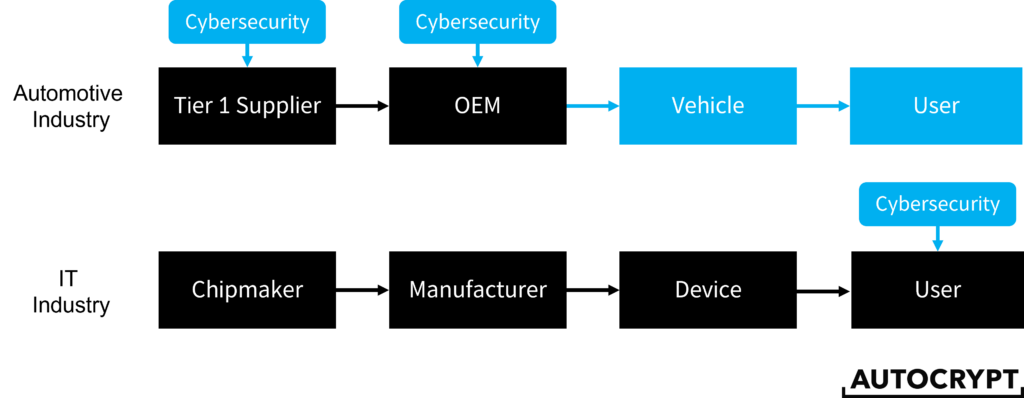
The biggest difference between vehicular cybersecurity and IT cybersecurity is that a vehicle does not run on a host computer, nor a unified operating system. Instead, each vehicle has a unique electronic and electric (E/E) architecture made up of over a hundred electronic control units (ECU), interoperating through the Controller Area Network (CAN bus). This means that there cannot be an off-the-shelf cybersecurity software or tool that is readily installable across all vehicles; instead, in-vehicle security needs to be custom-designed for each vehicle model.
To develop a system and process for a particular vehicle, it is crucial to start by assessing the threats associated with the specific OEM and vehicle model through an engineering methodology called Threat Assessment and Remediation Analysis (TARA). TARA is widely used for the initial assessment of cybersecurity risks, based on a deep analysis of the vehicle’s architecture, followed by a prediction of potential vulnerabilities and entry points. After identifying the risks, security engineers will thoroughly select a pool of necessary countermeasures that can mitigate these specific risks.
During TARA, AUTOCRYPT begins by identifying critical assets within the target vehicle, then compiles a list of attack vectors that hackers could potentially use to access and intrude the system. After that, the level of risk and feasibility of each attack vector is analyzed, before arriving at a final list of threat priorities. These priorities are used to design and develop a security model, where detection engines and software modules get embedded in different parts of the vehicle.
2. Threat Modeling and Security Testing
After initial design and development of the in-vehicle security system, it is then time to conduct a series of tests by simulating real-life hacking scenarios to verify the efficacy of the security model. In this stage, three types of security testing are implemented: vulnerability scanning, fuzz testing, and penetration testing.
Vulnerability Scanning
Unlike threat assessment in TARA, vulnerability scanning requires the physical vehicle prototype with the adopted security model. Both software static testing and dynamic testing are performed. The former checks for errors in the development stage, including leaks and buffer overflows, whereas the latter executes the code to test for vulnerabilities in runtime environments by analyzing the behaviours of dynamic variables.
Fuzz Testing
Fuzz testing, or fuzzing, is a type of automated software testing technique that feeds a large pool of randomly generated invalid and unexpected inputs into the program as an attempt to make it crash or break it through. If a vulnerability a found, a fuzzer can be used to pinpoint the potential causes. Fuzzing is a quick and useful way to identify unexpected coding errors, highly effective at mitigating most automated hacking techniques.
Penetration Testing
Penetration testing is the most advanced and sophisticated test of the three. It requires security analysts and red team hackers to manually search and exploit vulnerabilities using complex hacking techniques such as password cracking and injection, then try to manipulate and exfiltrate data from the vehicle. AUTOCRYPT’s red team, led by experienced resident white hat hacker Dr. Jonghyuk Song, performs penetration testing to vehicle components and security software prior to final implementation, ensuring that no vehicle leaves the factory in a vulnerable state.
After completion of threat modeling and security testing, all errors and vulnerabilities will be corrected and reviewed. Finally, the vehicle will be ready to enter the market.
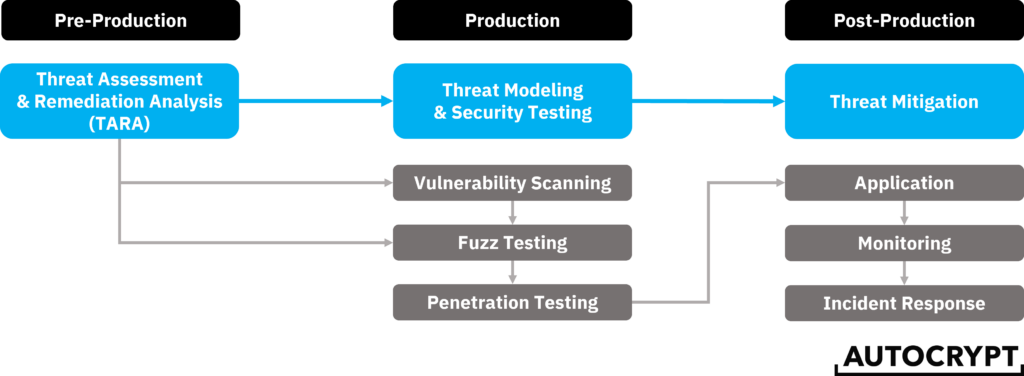
3. Threat Mitigation
As the vehicle gets passed down to the consumer, the role of cybersecurity does not end here. In fact, this is only the beginning of a long journey of continuous monitoring, prevention, and incident response. At this stage, the security engineering of AutoCrypt IVS works at its best to protect the ECUs by running both an intrusion detection system (IDS) and intrusion protection system (IPS) to block hacking attempts, encrypting all messages to prevent data tampering, and controlling access to all storages to ensure privacy and financial safety. It also monitors the central gateway for any abnormal behaviour throughout the vehicle’s CAN bus and between the vehicle to the external network. Such data is then collected in real-time by the OEM and reported to AutoCrypt vSOC (Vehicle Security Operations Center) for analysis.
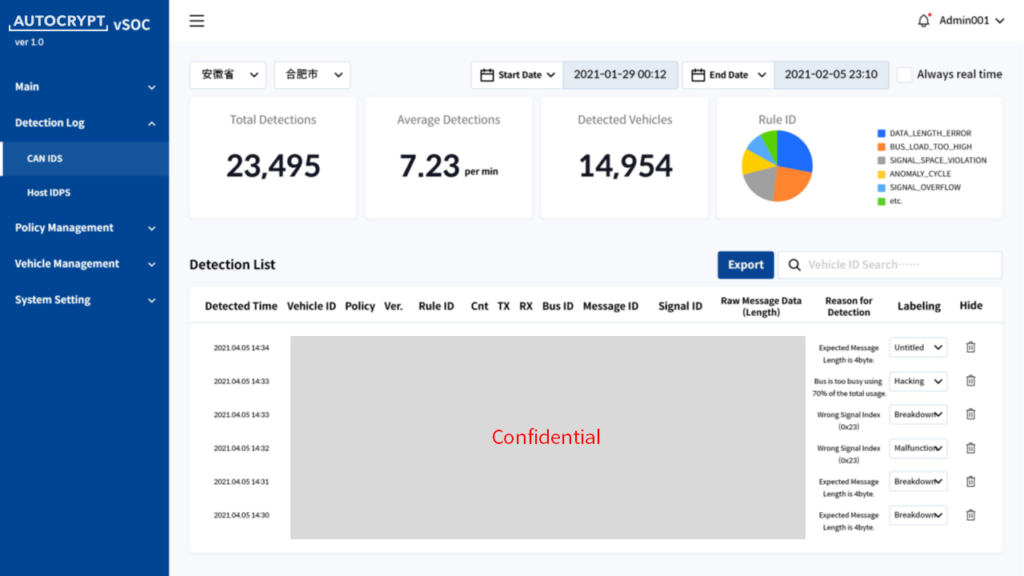
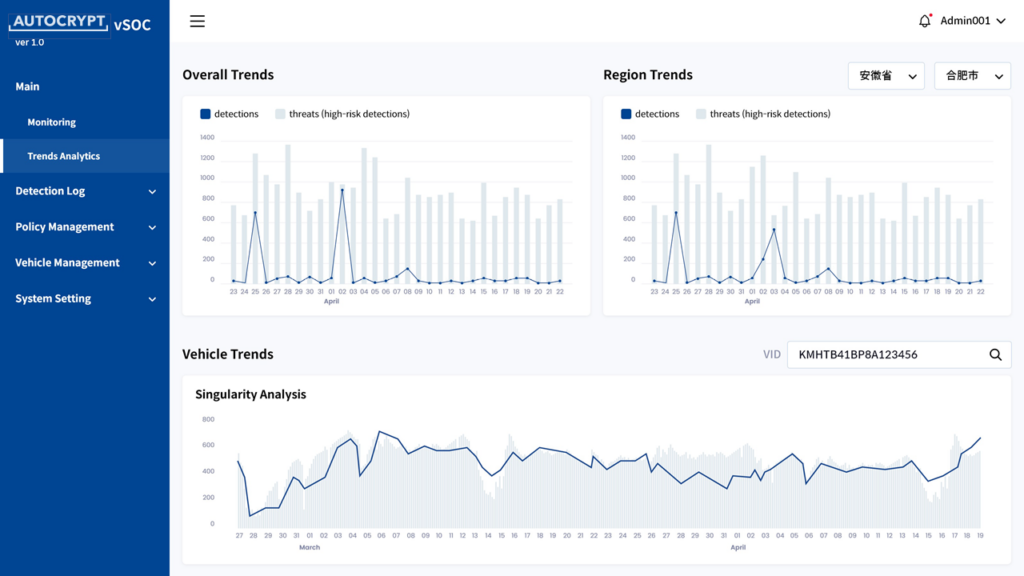
Vehicle Security Operations Center
Similar to the SOC in IT security, vSOC brings enterprise threat intelligence to the mobility environment by monitoring the activities and conditions of all active vehicles using live data collected and shared from the OEM’s cloud. AutoCrypt vSOC provides an easy-to-navigate graphical user interface, allowing the OEM to track and analyze threats by region and prioritize updates and patches.
Vehicular Cybersecurity Made Easy With AUTOCRYPT
Most OEMs do not have the time and capacity to assess, deploy, and manage all three stages of vehicular cybersecurity in-house. Over the past decade, AUTOCRYPT has been filling this gap not only by offering AutoCrypt IVS as a product, but also by designing and developing a complete in-vehicle security solution that OEMs can rely on in the long-run.
To learn more about AUTOCRYPT’s end-to-end solutions, contact global@autocrypt.io.
To stay informed with the latest news on mobility tech and automotive cybersecurity, subscribe to AUTOCRYPT’s monthly newsletter.