It has long been established that cybersecurity is essential to vehicle operations and needs to be implemented universally. However, it is important to note that automotive cybersecurity does not follow a one-size-fits-all approach. Different types of cybersecurity measures have their pros and cons and are more effective for certain types of vehicle architectures rather than others. While there are different types of vehicle cybersecurity measures available on the market today, this blog will discuss hardware security modules (HSM) and trusted execution environments (TEE), offering a closer look at two of the most robust vehicle cybersecurity solutions.
Why do we need in-vehicle security?
Modern vehicles have complex internal computing systems that enable superior functions like advanced driver-assistance systems (ADAS), vehicle-to-everything (V2X) communications, as well as network and cloud connectivity. These internal computing systems interact with each other and the external network, exchanging large amounts of data and signals. If these communication nodes lack appropriate security measures it leaves the vehicle vulnerable to cyber risk.
Wi-Fi, navigation systems, V2X communications, all of these network connection endpoints can be potential routes for cyber attacks. Hackers could breach into a vehicle’s internal system to steal private data like vehicle location, registration number, and even financial information. There is also the risk of hackers breaking into the vehicle systems to gain control of its functions. We saw this happen when two researchers hacked into a car through its cellular connection. After establishing a wireless access to the car, the hackers gained control of the vehicle’s dashboard, infotainment system, and even the engine.
This experiment revealed many vulnerabilities in vehicle internal systems security. It also solidified the importance of a layered approach to vehicle cybersecurity, where both the internal vehicle environment and the external communications are secured.
What is HSM?
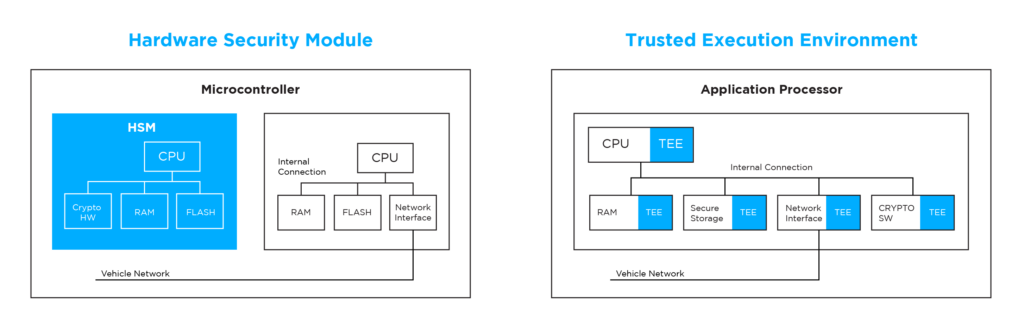
One of the most robust cybersecurity solutions in the automotive industry is a Hardware Security Module (HSM). HSM is an external physical security unit that is installed into electronic control units (ECU). It safeguards vehicle communications and functional control systems with message cryptography. Typically, an HSM will include its own processor, cryptographic technologies, and dedicated memory for the hardware security firmware and secure data. Having its own processor, the HSM operates separately from the ECU, bearing the computational load of security functions.
The security module’s main job is to safeguard sensitive vehicle data during message exchanges. It does this by storing cryptographic keys, performing cryptographic operations, and verifying digital signatures to conduct authenticity checks for messages passing through the vehicle. This makes sure that data coming from outside of the vehicle is verified, and data leaving the vehicle is safely encrypted.
HSMs have been the industry standard in vehicle cybersecurity for their ability to safeguard valuable information from tampering. However, there is a problem of scalability with this particular cybersecurity measure. HSM is a security unit that has to be physically installed into ECUs within the vehicle. So, installing HSMs in cars with complex internal architectures and an abundance of ECUs may become costly.
There is also the issue of flexibility. Many modern luxury vehicles support over-the-air (OTA) systems like software downloads and updates. These OTA systems enable the installation of new functionalities into a vehicle without having to alter its hardware composition.
In a rapidly developing automotive industry, cybersecurity software needs to be able to adapt to vehicle software changes. This will be hard to achieve for a car secured only with hardware security modules. The hardware-software segregation in advanced vehicle architectures requires a more flexible approach to cybersecurity that ensures cybersecurity measures evolve hand-in-hand with vehicle software developments.
What is TEE?
A cybersecurity solution that works more effectively in centralized vehicle architectures with ever-evolving software structures is a Trusted Execution Environment (TEE). TEE is a software-based security measure that creates a secure and isolated environment within the application processor, separating critical operations from the rest of the system.
Critical operations and sensitive data can be executed and stored within the trusted execution environment, shielded from potential cyber threats. Similar to HSMs, TEEs have protected crypto libraries where sensitive information, such as cryptographic keys, can be securely stored and managed. They also provide secure communication channels between trusted components, ensuring that data transmitted within the secured area remains confidential and protected from the rest of the vehicle. This helps prevent unauthorized access or tampering.
For instance, the AutoCrypt IVS-TEE security solution offers OTA systems security with encryption and authentication technologies, making sure that only validated software is received and installed during OTA system updates. This is done to ensure that the software comes from an OEM and not a malicious actor.
While TEE and HSM offer similar cybersecurity measures they are very different in terms of implementation and execution. TEEs are built into the application processor’s chipset and can be implemented through software updates, making them more flexible and adaptable to changing security requirements. Leveraging a vehicle’s existing hardware resources, TEEs eliminate the need for additional security components, potentially reducing costs.
Establishing a TEE is a cybersecurity-by-design approach that ensures that there is a secure environment to run critical operations in every application processor.
As vehicles become increasingly connected and autonomous, the importance of robust automotive cybersecurity methods cannot be overstated. HSM and TEE both play crucial roles in securing vehicles against cyber threats. HSMs excel in cryptographic operations and secure key storage, while TEEs create isolated execution environments within the main processor. By combining these methods, automotive manufacturers can maximize protection from external cyber threats and enhance the security of their vehicles.
AUTOCRYPT’s in-vehicle cybersecurity solutions provide complete protection for the vehicle-embedded systems minimizing cybersecurity risks.
To stay informed about the latest news on mobility tech and automotive cybersecurity, subscribe to AUTOCRYPT’s monthly newsletter.

![[AUTOCRYPT] CES 2026 Highlights](https://autocrypt.io/wp-content/uploads/2026/01/12_8-D-30_2-est-2.png)


