
The comprehensive cybersecurity solution for vehicle production.
An intrusion of in-vehicle systems can be silent yet catastrophic. By gaining entry into the in-vehicle infotainment (IVI) or the telematics control unit (TCU), hackers could make their way into critical CAN buses and ECUs and tamper with communications within and beyond the vehicle. A successful attack could lead to data theft, location exposure, vehicle theft, and even vehicle hijacking.
AUTOCRYPT’s comprehensive In-Vehicle Systems Security solution (branded as AutoCrypt® IVS) uses proprietary cybersecurity technologies and intelligence to protect vehicles at all three stages: development, production, and post-production. Built for both AUTOSAR and legacy environments, and designed in compliance with ISO/SAE 21434 and the UNECE WP.29 regulations, AUTOCRYPT ensures its clients are ready for type approvals and its end-users are safely protected.
AUTOCRYPT’s In-Vehicle Systems Security solution covers the following:
TARA (Threat Analysis and Risk Assessment)
Software composition analysis and licence management
Smart fuzzing (applicable in HIL simulations)
Penetrating testing (by award winning Red Team)
Embedded security software (IDS, HSM, ASL, TEE)
Highlights
All you need to know about in-vehicle systems security
and stay prepared with AUTOCRYPT
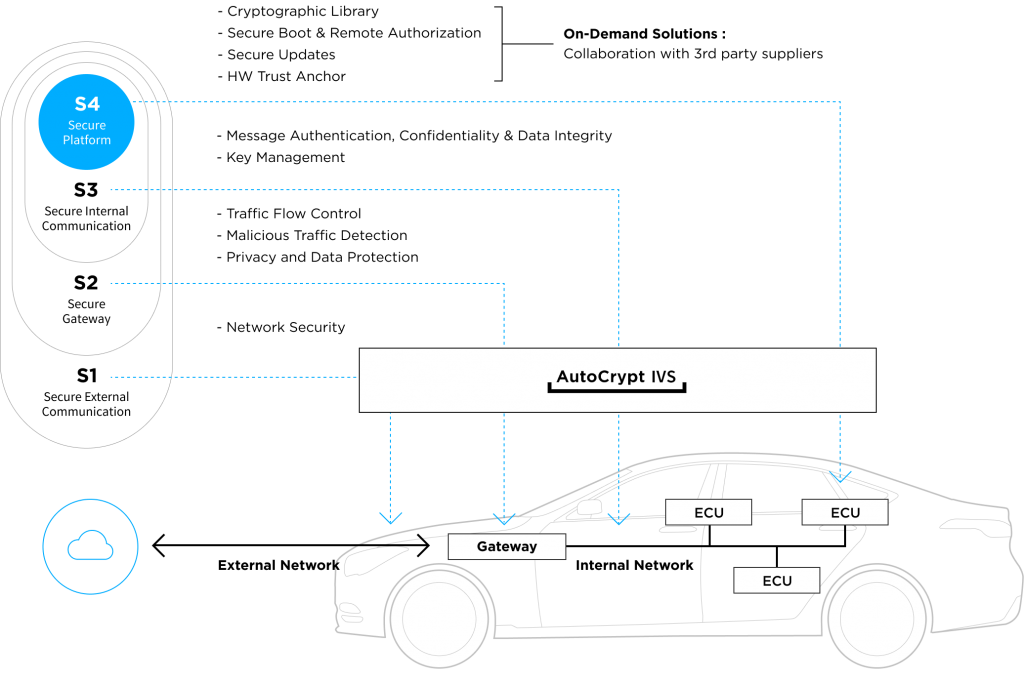
In-Vehicle System Structure
A vehicle’s internal system consists of over 100 ECUs (electronic control units), which control a number of electrical subsystems responsible for all functionalities of the vehicle, from handling to connectivity.
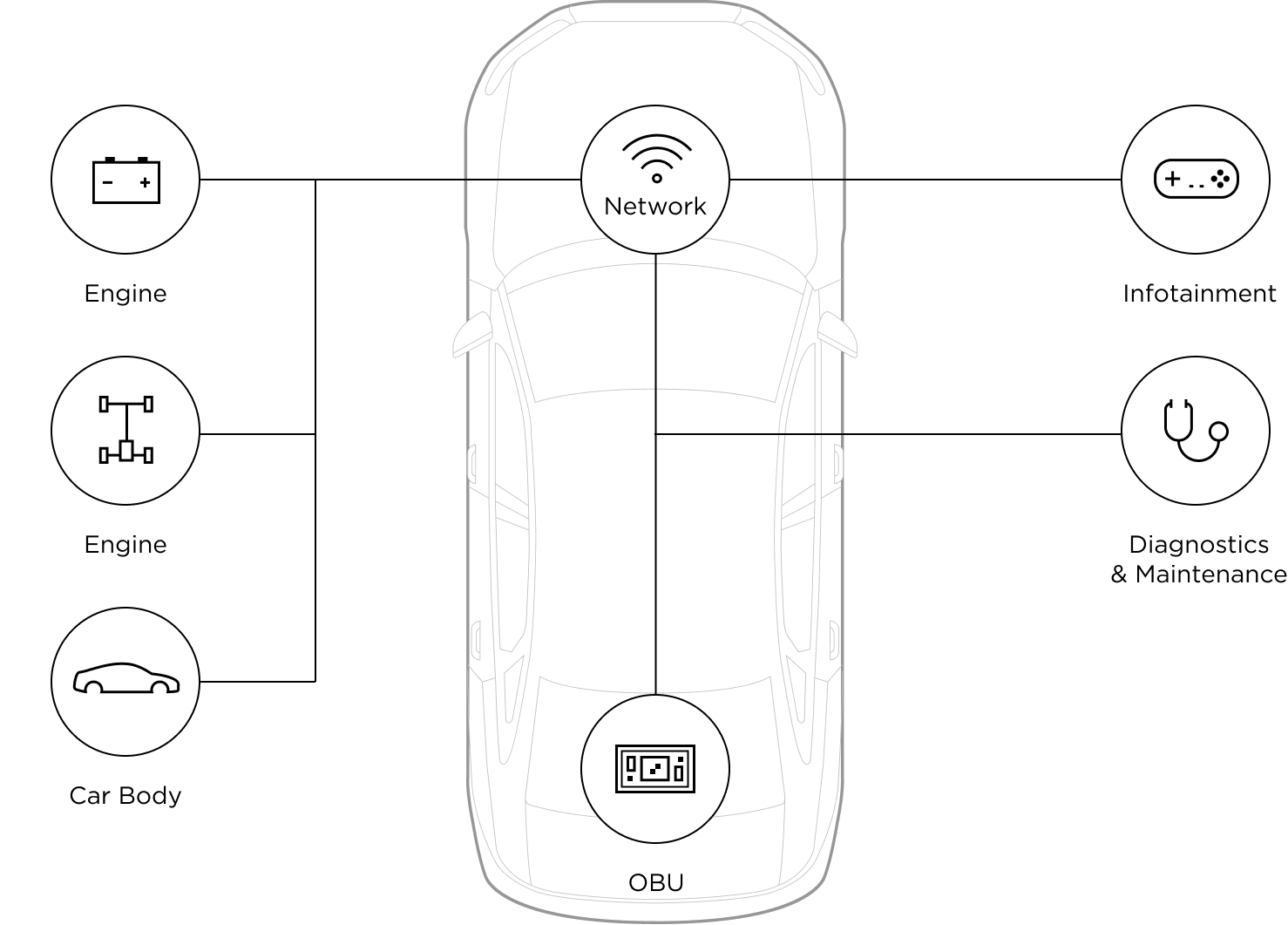
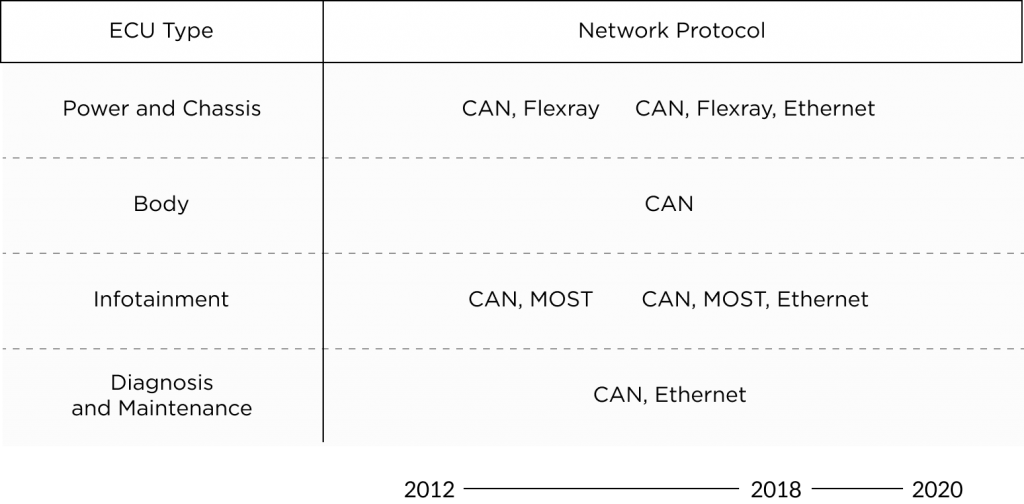
The CAN (Controller Area Network) and MOST (Media Oriented System Transport) are two primarily used network protocols that enable communications between the ECUs. The CAN buses facilitate a vehicle’s internal communications for controlling power, direction, braking, etc., while MOST enables the systems for transmitting in-vehicle audio, video, and data via fiber-optic cables.
Other network protocols like FlexRay and Ethernet govern high-capacity onboard computing.
Need for Security
The CAN (Control Area Network) bus is designed to allow microcontrollers and in-vehicle systems to communicate without a host computer.
However, they are not built with the intention of tracking where the communicated messages come from, making the systems vulnerable to external threat actors.
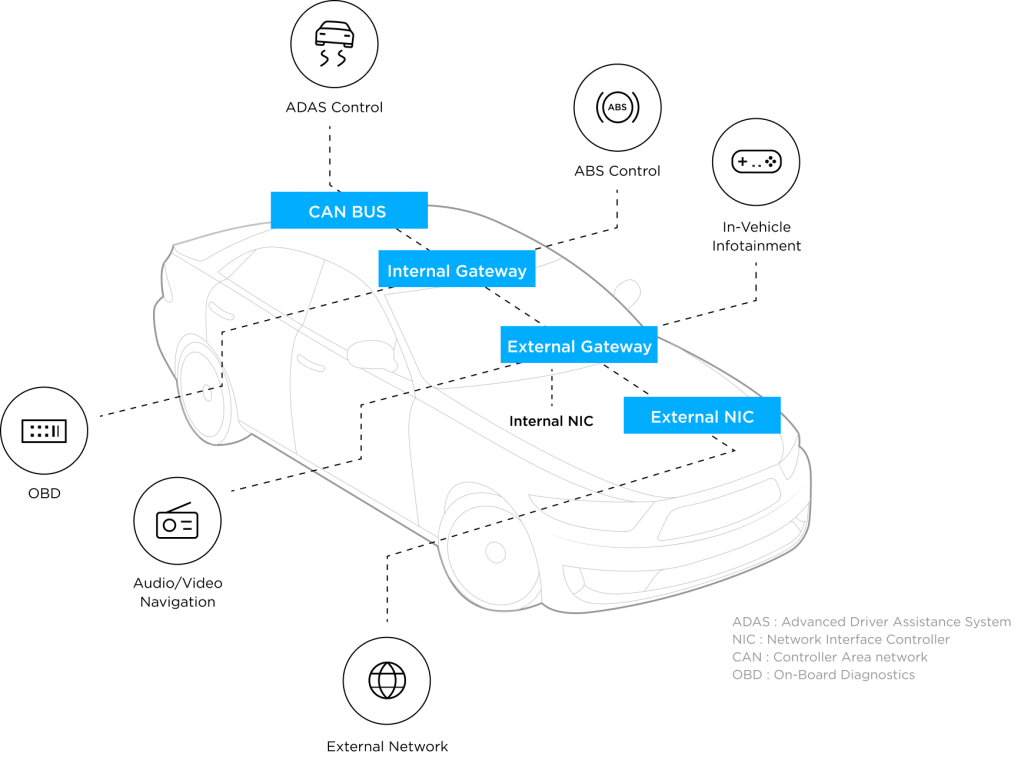
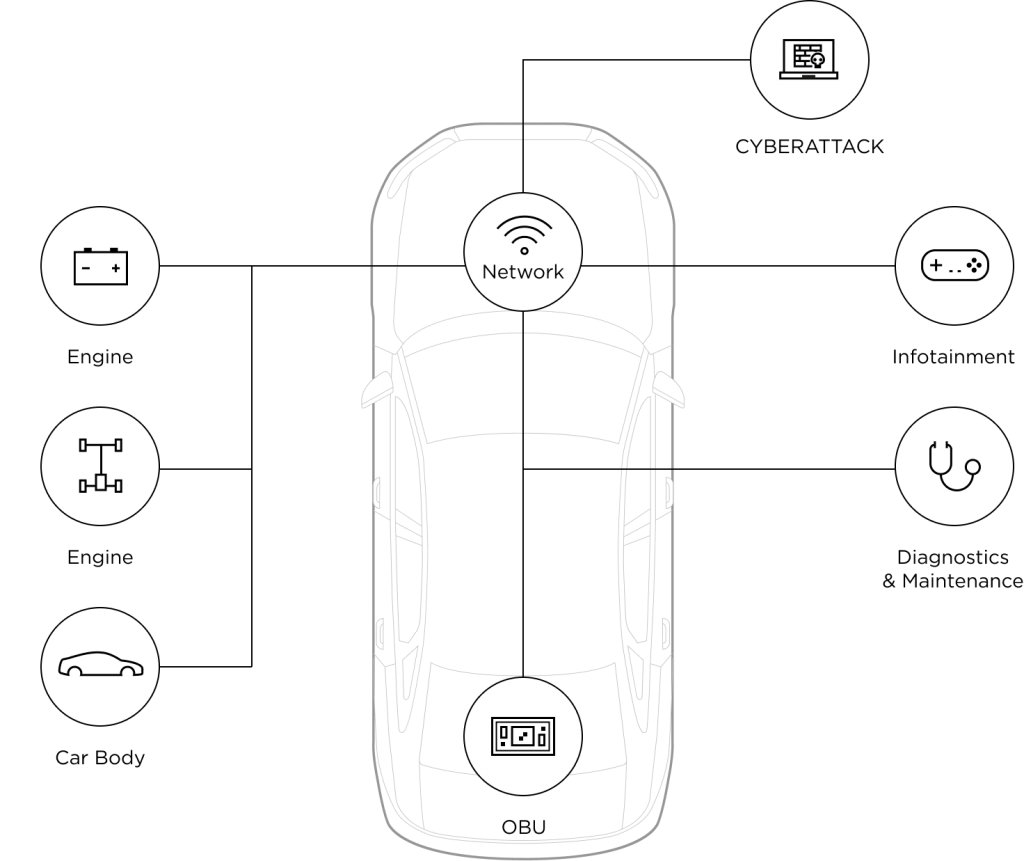
If an attacker were to take over an ECU by exploiting vulnerabilities in the network, they would be able to control certain parts of the vehicle using forged data or injecting malicious code, as well as gain access to sensitive information.
Hackers may attempt to establish a foothold in the vehicle’s various embedded systems by executing attacks that make changes to the memory disk, damage the ECU functions, or infiltrate the core data storage units of the vehicle.
2010. 08 | Message fabrication from tire-pressure monitoring system (TPMS) resulting in false activation of warning lights and announcing false system failure in ECU systems
AUTOCRYPT's In-Vehicle Systems Security Solution
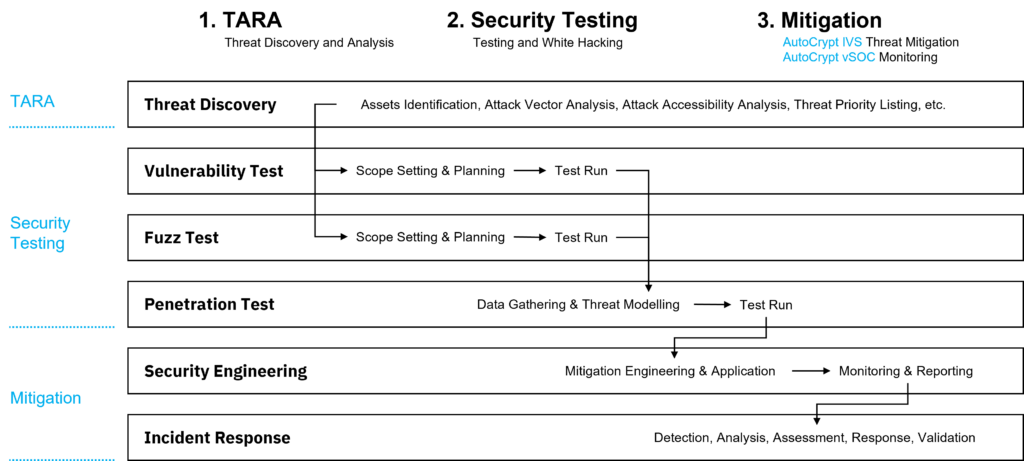
AUTOCRYPT’s In-Vehicle System Security solution provides complete protection for the embedded systems of a vehicle through a three-step process from 1) TARA, 2) Security Testing, and 3) Mitigation and Monitoring.
AutoCrypt® IDS monitors communications within the vehicle, responding to any abnormal or malicious activities using its proprietary Security Sensor.
In-Vehicle System Security Products

AutoCrypt IDS
A vehicular intrusion detection solution that detects, filters, and prevents cyberattacks against in-vehicle systems. It consists of an N-IDPS and an H-IDPS, complemented by event reporting, automated policy generation and simulation.

AutoCrypt HSM
A software module that seamlessly integrated the hardware security module (HSM) into the AUTOSAR environment, ensuring the secure access of ECUs and acting as a trust anchor for in-vehicle communications.

AutoCrypt Security Analyzer
A software vulnerability analysis platform that generates the software bill of materials (SBOM) through function-level analysis, allowing for continuous vulnerability management and patching throughout the entire software development lifecycle (SDLC).

AutoCrypt Security Fuzzer
A smart fuzzing tool that accurately and effectively detects software coding flaws by repeatedly feeding AI-generated random inputs.
AutoCrypt ASL
An adaptive security library designed for the AUTOSAR Adaptive Platform, ensuring security for high-performance ECUs, such as in-vehicle application servers, infotainment systems, and ADAS.

AutoCrypt TEE
An ASPICE CL2-certified in-vehicle systems security solution that utilizes a trusted execution environment (TEE) to protect SoC platforms like ADAS, IVI, and CCU.

Related Service
WP.29 Consulting
AUTOCRYPT helps you prepared for all the cybersecurity requirements needed for vehicle type approval under the UNECE WP.29 regulations.

About AUTOCRYPT
AUTOCRYPT
AUTOCRYPT is a mobility security provider with the goal of providing a seamless and secure mobility experience for all.

