Building on our previous post examining the industry’s transition from SAE Level 2 to Level 3 autonomy, this article revisits the topic in light of regulatory and commercial developments around autonomous driving. Our earlier analysis found that the slow progession toward Level 3 autonomy has been driven more by regulatory uncertainty than by technological limitations. Due to ongoing legal bottlenecks, we observed that OEMs introduced Level 2+ systems but remain hesitant to classify them as Level 3, primarily because of unresolved concerns around legal responsibility and risk management.
Since then, the regulatory and commercial landscape for autonomous driving has continued to evolve. This article highlights how recent policy shifts have accelerated Level 3+ deployment and testing efforts, while also examining the growing importance of open-source software in enabling software-defined vehicle (SDV) development. As SDVs grow more complex — both technically and in terms of regulatory oversight — it has become essential for OEMs and Tier 1 suppliers to stay aligned with ongoing developments and adapt their cybersecurity practices accordingly.
Bridging Regulation and Deployment in Autonomous Driving
As commercial interest in Level 3+ autonomy grows, regulatory developments have played a pivotal role in shaping a more stable legal environment for innovation. Both globally and regionally, recent updates have provided clearer guidelines for deployment, liability, and compliance. Among the most impactful are the ongoing amendment series to UNECE Regulation No. 157 on Automated Lane Keeping Systems (ALKS) and the introduction of UNECE Regulation No. 171 on Driver Control Assistance Systems (DCAS).
Global Regulatory Progress in Autonomous Driving
The UNECE Regulation No.157 on Automated Lane Keeping Systems (ALKS) was first adopted by the World Forum for Harmonization of Vehicle Regulations (WP.29) in January 2021 to govern SAE Level 3 conditional automation. Since enforcement began in January 2023, successive amendments introduced from 2022 onward have significantly clarified the operational behavior, system safety, and failsafe protocols required for real-world applications.
- WP.29/2022/59/Rev.1 Amendment: Speed limit raised from 60km/h to 130km/h, Automated lane changes allowed
- WP.29/2024/145 Supplement: Ensure ALKS system resilience in electromagnetic environments
- WP.29/2025/64 Supplement: Clearer rules for lane-change behavior and heavy vehicle restrictions
In parallel with ALKS, UNECE Regulation No.171 on Driver Control Assistance Systems (DCAS) established safety requirements for SAE Level 2 driver assistance features, including lane keeping and traffic jam assist. The regulation emphasizes stricter standards for driver engagement, monitoring systems and interface transparency. Together, these two frameworks — covering foundational technologies like ALKS and DCAS — have strengthened the regulatory pathway towards higher levels of autonomy by mandating provisions for cybersecurity, performance validation and over-the-air (OTA) updates.
Regional Regulatory Advances around Autonomous Vehicles
At the regional level, China and Germany have taken leading roles in building regulatory frameworks for autonomous vehicles, while the United States and South Korea have also made notable progress in deployment and certification efforts.
China introduced a clear commercialization pathway for OEMs targeting Level 2-4 autonomy through its national pilot program, announced in November 2023. By focusing on seamless integration between vehicles, infrastructure and cloud platforms — leveraging technologies such as Cellular Vehicle-to-Everything (C‑V2X), edge computing, and signal systems — the initiative has ensured pilot zone vehicles are equipped for safe and standardized evaluation.
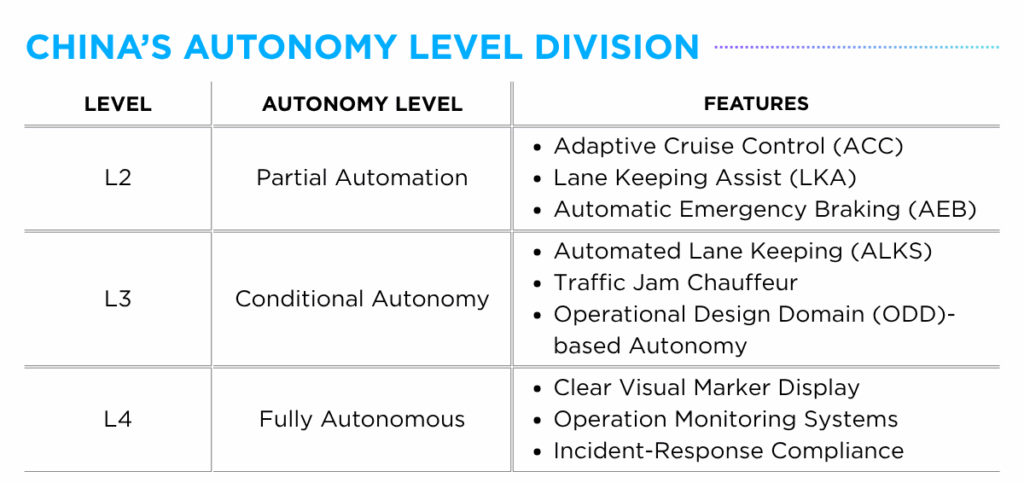
Through this initiative, Chinese OEMs have made significant progress, launching their own branded ADAS platforms — DiPilot (BYD) and G-Pilot (Zeekr) — in early 2025. BYD became the first Chinese automaker to obtain a conditional Level 3 testing license in July 2023 and has since introduced Level 4 autonomous parking capabilities through its DiPilot ADAS platform. By June 2025, nine manufacturers, including Nio, Changan Automobile, and GAC, had completed preparations for public road testing of Level 3-capable vehicles.
Germany has also emerged as a regulatory leader, particularly through the Autonomous Vehicles Approval and Operation Ordinance (AFGBV) which governs the approval, registration and operation of SAE Level 4 autonomous vehicles. While the ordinance was adopted in May 2022 and came into effect in July 2022, detailed implementation guidelines published in 2024 clarified practical procedures for public transportation authorities. These documents have provided essential guidance to municipalities, transit operators and OEMs, helping shape a consistent framework for the long-term deployment of autonomous fleets.
- Guideline for Operational Area Approval: Framework for municipalities and OEMs to define, assess, authorize public road areas for autonomous vehicle operation
- Handbook with Implementation Proposals for Municipal Practice: Offers integration guidance for public transport operators
- Strategy for Autonomous Driving in Road Traffic: Outlines Germany’s national roadmap for autonomous vehicle (AV) deployment across mobility and infrastructure sectors
These regulatory advances have enabled OEMs such as BMW and Mercedes-Benz to integrate automation software into their vehicle portfolios. In June 2024, BMW introduced both Level 2 (‘BMW Highway Assistant’) and Level 3 (‘BMW Personal Pilot’) systems in its 7 Series lineup, offering highway automation and conditional driver delegation capabilities. In December 2024, Mercedes-Benz received approval to increase the operating speed of its DRIVE PILOT system to 95km/h and became the first automaker in Germany authorized to use special marker lights indicating automated driving mode.
Beyond China and Germany, regulatory clarity has expanded in other key regions. In South Korea, a March 2025 update to the enforcement decree of the Act on the Promotion and Support for the Commercialisation of Autonomous Vehicles enabled performance certification and approval of Level 4 autonomous vehicles, including those lacking pre-established safety standards. Similarly, the United States broadened Federal Motor Vehicle Safety Standards (FMVSS) exemptions under Part 555 in June 2025, allowing developers to deploy safety-validated autonomous vehicles that do not meet conventional design requirements.
These national and international efforts collectively signal a growing global alignment in regulatory strategy and commercial deployment readiness. Structured permit systems and clearly defined liability frameworks have provided OEMs with the flexibility to develop, certify, and scale Level 3+ autonomous vehicles — a momentum that is likely to accelerate further in the coming years.
Open-Source SDV: Software-Driven Collaboration
As the path to commercial autonomy becomes clearer, attention is increasingly turning to the software foundations that enable it to scale — particularly open-source software defined vehicle (SDV) projects. This shift is being shaped by the growing convergence of autonomous vehicles (AVs) and SDVs, where AVs increasingly rely on SDV architecture for modularity, real-time updates, and system integration. Open-source platforms are emerging as critical enablers of this transition by supporting scalable and collaborative development.
SDV platforms provide the technical backbone for scalable autonomy by enabling modular design, continuous over-the-air (OTA) updates, and real-time system integration. These capabilities, when delivered through accessible and interoperable open-source solutions, help overcome the fragmentation and integration challenges that often hinder large-scale AV deployment.
A key example of this trend is the S-CORE Project, announced in June 2025. Backed by key industry players like Bosch, QNX and Mercedes-Benz, the initiative aims to build the first open-source core stack for SDVs. The core stack is designed to standardize the middleware layer between the operating system and higher-level vehicle applications, with an emphasis on functional safety. Aligned with global regulatory standards such as ISO 26262 (functional safety), ISO/SAE 21434 (cybersecurity), and UN Regulation No. 156 (OTA Updates), the framework is OEM-agnostic and modular by design — supporting deployment across a wide range of vehicle platforms.
While it builds on a growing legacy of open-source automotive projects such as Autoware — of which AUTOCRYPT is a participating member focused on addressing security risks in real-world vehicle software — the S-CORE Project represents a meaningful shift. It moves focus from application-specific tools (e.g., AV stacks, ADAS platforms) toward foundational, certifiable infrastructure designed to support mass production of SDVs. Positioned as a “core runtime environment” for software-defined vehicles, S-CORE aims to bridge the gap between low-level system layers and OEM-specific applications, creating more room for OEMs and Tier 1 suppliers to collaborate on shared infrastructure.
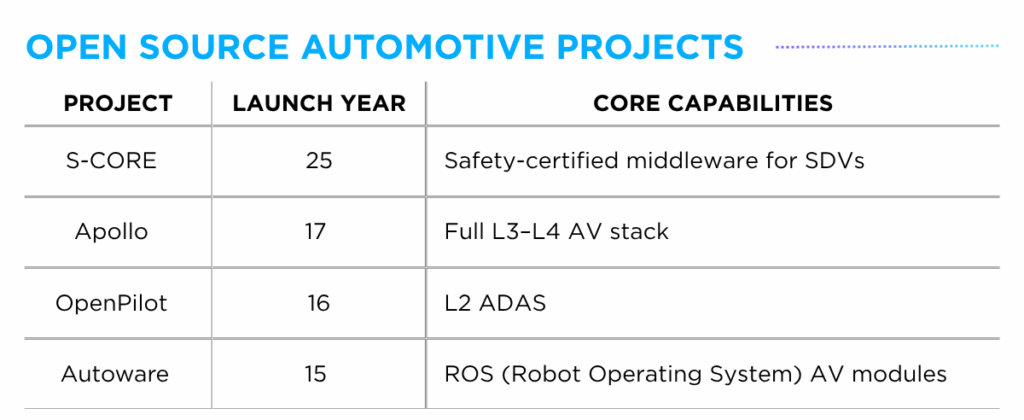
Further open-source projects around software-defined vehicles are expected to emerge in the future due to economic and strategic industry alignment. With the complexity of software-defined vehicles (SDVs) increasing, it has become less viable for individual OEMs and/or suppliers to build and maintain fully proprietary software stacks. Open-source core frameworks like the S-CORE project aim to address this challenge by providing a standardized, resuable foundation which could allow companies to redirect resources toward value-added differentiation (UX, apps, mobility features).
Alignment with global regulatory standards has further elevated the role of open-source software. Standards such as UNECE R156 and R157, ISO 24089, ISO/SAE 21434 emphasize the need for secure, traceable, updateable vehicle software, better done transparently through building on open-source environments. In short, open-source projects offer a flexible and accountable framework, helping stakeholders align with evolving requirements more efficiently.
Future Implications
Regulatory and commercial developments across Levels 2 to 4 autonomy continue to mature, creating new opportunities for OEMs and Tier 1 suppliers, while steadily enhancing the autonomous driving experience for end users. This transformation is no longer confined to national borders, as open-source initiatives gain traction, driven by economic and regulatory imperatives.
As autonomous driving environments expand, so do the associated attack surfaces — from internal vehicle systems to connected external infrastructure. This underscores the growing need for continuous cybersecurity validation, including threat modeling, real-time risk monitoring and regulatory gap analysis. Positioned at the intersection of software-defined vehicle (SDV) innovation and autonomous vehicle (AV) safety, Autocrypt remains committed to supporting OEMs and Tier 1 suppliers in scaling innovation without compromising cybersecurity.
To learn more about the Autocrypt’s products and offerings, click here. Read our blog or subscribe to AUTOCRYPT’s newsletters for more technology insights.