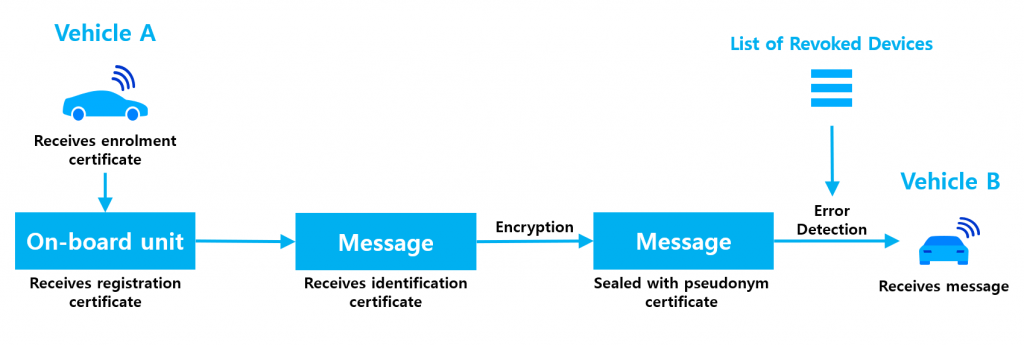
In a previous article DSRC vs. C-V2X: A Detailed Comparison of the 2 Types of V2X Technologies, we explained the differences between DSRC and C-V2X. We mentioned that since these two technologies rely on different wireless communication protocols, there has been no controlled side-by-side comparison on their efficacy. Despite so, based on their real-world usage today, the consensus is that both DSRC and C-V2X are fully capable of direct V2X communication.
However, industry policymakers, infrastructure developers, along with automotive manufacturers, are still racing towards C-V2X deployment even though DSRC is a more mature technology that has already undergone all testing stages. The reason for favoring C-V2X, as we stated last time, is that despite both technologies having similar capabilities today, it is unlikely to remain so in the future. Those in favor of C-V2X argue that the technology provides more room for future improvements and will eventually be much more useful than DSRC.
Hence, in this article, we will explain what exactly the potentials of C-V2X are, starting with the table below:
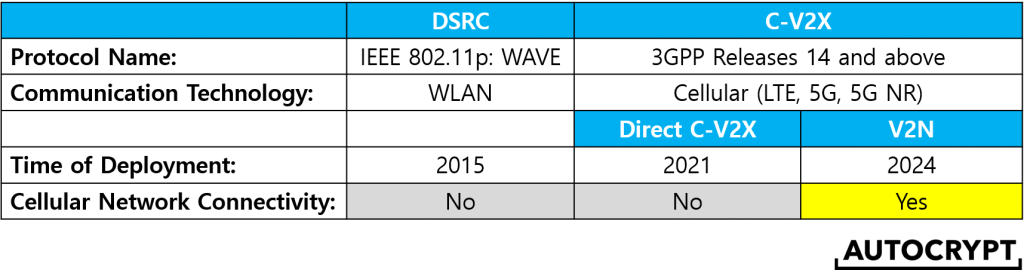
On the right side of the table, we can see that C-V2X can be broken down into two different modes. The first is direct C-V2X mode. Utilizing the PC5 interface, direct C-V2X is based on unicast communication and operates under the same mechanism as DSRC does. In other words, it enables a vehicle to directly send and receive wireless messages to and from other vehicles and roadside units, given that they are within a certain distance. This kind of unicast communication is what V2X was originally meant for.
All the potentials of C-V2X lie in its second mode, V2N (vehicle-to-network) mode. V2N utilizes a network communications interface called the Uu interface, which essentially enables broadcast communication via existing cellular mobile networks. The ability to connect to the mobile network is a crucial feature that WLAN-based DSRC technology cannot provide. The illustration below shows how direct C-V2X and V2N work together.
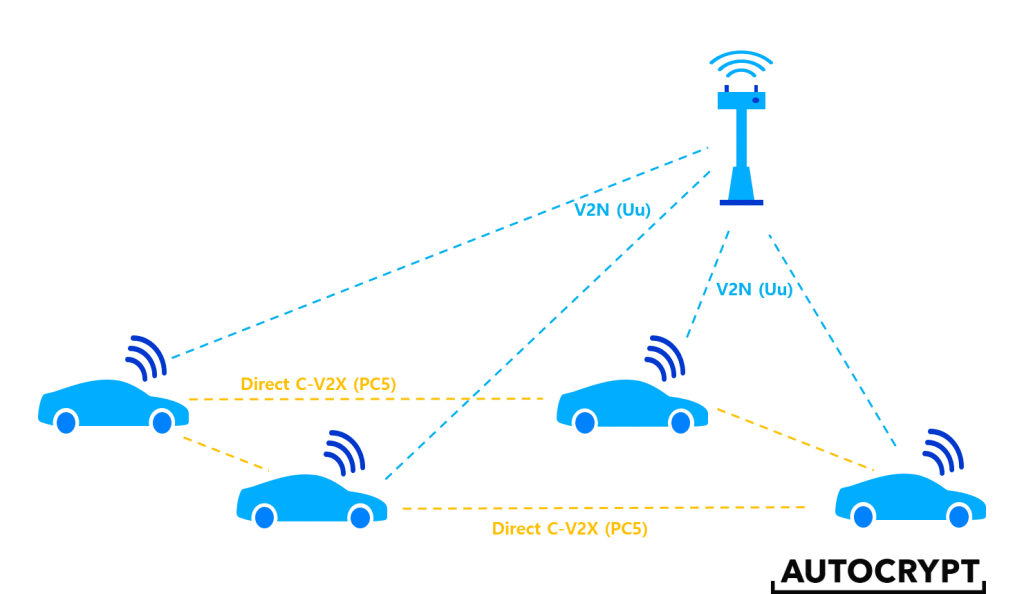
Despite all the potentials, V2N technology is not ready for deployment until around 2025. Without V2N, direct C-V2X and DSRC are very comparable in the meantime. Thus, many automakers still choose to implement DSRC in the short run given all the sunk cost invested into the technology.
Nevertheless, key industry players are developing C-V2X to keep themselves prepared for the game-changing potentials of V2N, because broadcast communication will certainly take mobility to the next level.
V2N and Its Potential Benefits
Direct V2X technology – both DSRC and direct C-V2X – is quite capable of ensuring a safe and seamless autonomous driving experience. Then why do we still want to connect vehicles to the mobile network? Skeptics believe that V2N is the result of mobile network operators lobbying policymakers to secure themselves a new revenue source. This is undeniably one of the driven forces for V2N, but there are also many other positive reasons for adopting V2N.
Easy and cheap implementation. Implementing V2N is not difficult. Since V2N operates via cellular mobile networks, a large part of the physical infrastructure is readily available. Most urban areas already have LTE-capable cell towers and are slowly upgrading into 5G infrastructure. If we need the very same technology to provide internet connections for smartphones and IoT, we might as well just use it for vehicles – there is very little reason to not use a technology that is readily available. Additionally, adopting V2N is relatively cheap because both the PC5 and Uu interface can be easily combined into a single C-V2X chipset. Therefore, automotive OEMs and infrastructure developers do not need to spend extra to enable both modes.
Smoother traffic. Cooperative Intelligent Transportation Systems (C-ITS) rely on real-time data sharing to make traveling on the road safe and seamless. When all cars are connected to a mobile network, it becomes easier for C-ITS to provide timely and reliable information about traffic conditions and road hazards. For instance, under DSRC or direct C-V2X, cars will only receive information on the approach of an ambulance when it approaches within a few hundred meters. This may not be a sufficient distance to ensure every vehicle gets out of the way in time, especially under heavy traffic. However, when all vehicles are connected to the mobile network, the entire traffic can prepare for emergency situations well ahead of time.
More powerful route planning. Again, since DSRC and direct C-V2X only allow a vehicle to communicate with nearby units that are within a “relevant” distance of usually 300 to 500 meters, it cannot foresee situations beyond this limit. Even though this distance is sufficient to ensure a safe and smooth experience at the current moment, it does not help interactive route planning because it is not possible to project the traffic flow on the roads far ahead. V2N can help autonomous vehicles to plan well ahead of time and choose optimized routes based not only on real-time traffic information, but also based on projected future traffic from the planned routes of other vehicles.
Economies of Scale. V2N enables the collection of vehicle and traffic data into cloud servers. Having such enormous panel data is especially helpful for road infrastructure improvement. After machine learning, AI-generated predictive models can be used to calculate optimized solutions for adjusting the lengths of traffic lights based on time of day or variating speed limits based on weather condition. The big data also open a world of new opportunities and business models that can be integrated with the in-vehicle infotainment system, along with other possible features such as interactive parking, wireless car payment, and more.
Faster speeds. Since C-V2X is upgradable into 5G and 5G NR protocols, V2N will always be on par with the latest and fastest internet speeds available. Clearly, the speed of communication is a very crucial factor in autonomous driving safety. 5G and 5G NR chipsets will also allow vehicles to communicate with smartphones in a timely manner, truly enabling V2P (vehicle-to-pedestrian) communication, which would remarkably improve pedestrian safety and save millions of lives.
AutoCrypt V2X, the Foundation for the Future of V2N
Whether it be DSRC or C-V2X, cybersecurity is the foundation that keeps these technologies evolving. As V2N connects the entire world of traffic via the cellular mobile network, the industry is expected to face unprecedented cybersecurity threats. AUTOCRYPT takes this threat very seriously. AutoCrypt V2X has been working with OEMs and smart infrastructure projects around the world. With profound expertise in encryption and PKI technology, it plays a crucial role in building a safe environment for V2N.
To keep informed with the latest news on mobility tech and automotive cybersecurity, subscribe to AUTOCRYPT’s newsletter.