In 1939, the idea of the autonomous vehicle (AV) was brought to life by Norman Bel Geddes when he introduced the concept of a self-driving car in a futuristic exhibit hosted by General Motors (GM). Geddes conceptualized the car to be able to “drive” by radio-controlled electromagnetic fields generated with magnetized spikes that were embedded in the roadway. Although it may have been a bit early for realizing his AV dreams, the actual technology used in building vehicles with the potential of reaching full autonomy has developed rapidly in the past decade. Although we are yet to produce fully autonomous vehicles (level 4 or above), the AV landscape is expanding at a faster-than-ever pace. With this growing landscape comes wider adoption – more and more countries are allowing AVs on the roads, though they vary in terms of regulation and guidelines. Here are some global regulations on autonomous vehicles.
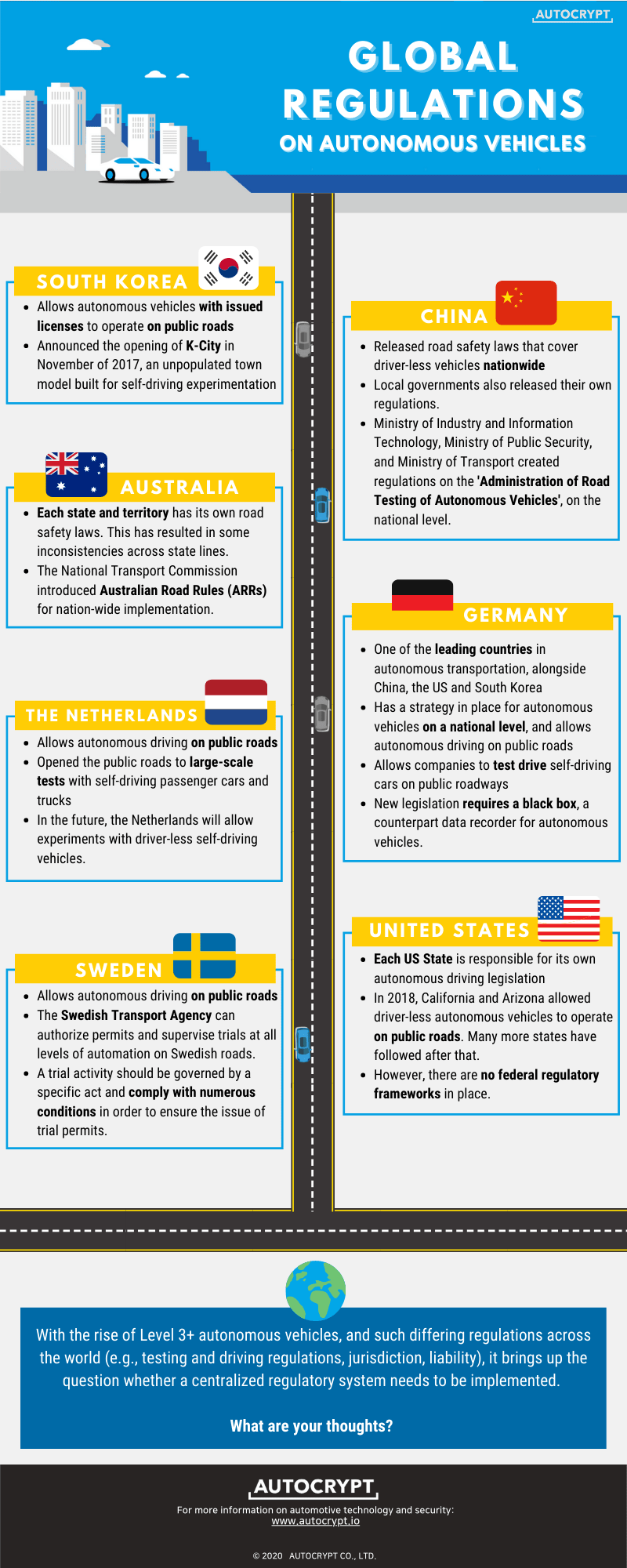
South Korea
South Korea allows AVs with government issued licenses to operate on public roads. As one of the leading countries in the AV industry, it announced the opening of K-City in 2017, which is an unpopulated town model built solely for autonomous-driving testing. The test-bed is the first of its kind in the nation and the second largest in the world. AUTOCRYPT is the security leader of the ITS-project, and the security company also manages V2X security for smart roads in Sejong, Yeoju, Seoul, and Jeju.
United States
The United States has a unique governing system where each state can publish its own legislation; as such, each US state is responsible for its own autonomous driving laws. There were no set rules about driver-less AVs operating on public roads before 2018 when California and Arizona passed legislation allowing for AV operation. Many other states have followed since then.
China
China has released a then-updated road safety laws that cover driver-less vehicles on a nationwide scale. The Ministry of Industry and Information Technology, the Ministry of Public Security, and the Ministry of Transport created regulations on the “Administration of Road Testing of Autonomous Vehicles.” In addition, local governments added their own regulations accordingly.
Germany
As one of the leading countries in autonomous transportation, alongside China, the US, and South Korea, Germany has a strategy in place for AVs on a national level and allows autonomous driving on public roads. Additionally, it allows companies to test drive autonomous cars on public roadways. However, the new transportation legislation requires all AVs on public roads to have a black box equipped, a counterpart data recorder.
The Netherlands
The autonomous transportation laws of the Netherlands allow for autonomous driving on public roads, and it also opened the public roads to large-scale tests with autonomous passenger cars and trucks. In the future, the Netherlands will allow experiments with driver-less AVs.
Sweden
Sweden, too, allows autonomous driving on public roads. Moreover, The Swedish Transport Agency can authorize permits and supervise trials at all levels of automation on Swedish roads. To ensure the issue of trial permits, however, the trial activity should be governed by a specific act and comply with numerous conditions specified further on the agreement form.
Australia
In Australia, each state and territory has its own road safety laws, and this has resulted in some inconsistencies across state lines in the past. The National Transport Commission introduced Australian Road Rules (ARRs) for nationwide implementation.
Many more countries have introduced AV regulations, but with the rise of level 3+ autonomous vehicles, we also see an increase in the reported number of accidents caused by and involving vehicles that are put on the autonomous-driving mode. With such differing regulations across the world in terms of testing and driving regulations, jurisdiction, or even liability, it brings up the question of whether a centralized regulatory system needs to be implemented.
Global regulations may continue to change as technology evolves and develops. What are your thoughts?