With the rapid rise of products utilizing AI, IoT, and connected technology, there has been growing concern across all industries of the cybersecurity risks associated with embedded technology. In response, in December 2024, the European Union put into force the Cyber Resilience Act (CRA), aiming to raise the baseline for security for all digital products and solutions sold in the EU.
Though the regulation originated in Europe, its impact will be global, as today’s interconnected market and supply chain crosses borders. Here’s a closer look at the CRA, why it matters, and its implications on the world’s automotive sector.
What is the Cyber Resilience Act?
The CRA is a legal framework that outlines cybersecurity requirements for products (both hardware and software) with digital elements sold within the European Union. The CRA casts a much wider net than requiring cybersecurity for traditional IT systems, covering everything from smart watches, refrigerators, to agricultural vehicles. In fact, the regulation not only applies to the products themselves, but the full lifecycle of IoT and digital products.
The objective of the CRA is to improve consumer safety, build trust in the digital marketplace, and ensure that manufacturers are held accountable for the security of their products. With this overarching regulation, the hope is that the CRA will foster more transparency for the digital ecosystem, ultimately encouraging innovation while still protecting both businesses and consumers from emerging cyber threats.
The CRA mandates a “security-by-design” approach, which means that companies must integrate cybersecurity from design through the end-of-life (EOL). It also requires vulnerability management and updates, along with compliance and documentation.
Key Implications for Industries Utilizing Connectivity
More and more industries are implementing connected technologies into their supply chain, which means the CRA targets a wide range of industries, including defense, IT infrastructure, and robotics/smart factory, to name a few.
Healthcare & Medical Devices: Many healthcare products now boast connectivity and dedicated user support. Products like remote monitoring tools, smart implants, and other medical devices must secure processed data and ensure device integrity.
Smart Manufacturing: Factories often use IoT and smart automation to optimize their factory lines. Networks and real-time operations must protect against cyberattacks that could disrupt industrial processes.
Space & Defense Systems: Satellites and mission-critical technologies must use robust protection to safeguard against cyber threats and protect sensitive operations for national security.
Agricultural Machinery: Like connected vehicles, agricultural transport is becoming much more connected and software-driven, meaning vehicles like autonomous tractors and sensor-based farming equipment must comply with the CRA as well.
CRA: More than the Law
The CRA represents more than just regulation within the EU. It signals a global shift towards mandatory cybersecurity standards for connected solutions, including all types of vehicles. Early preparation will be key, as manufacturers must utilize security-by-design principles from the development stage of all products.
The CRA introduces a risk-based product classification system, allowing a transition period until December 2027 for full compliance.
A lack of cybersecurity resilience increases likelihood of a cyber attack, which can not only lead to operational disruption and financial loss within a company’s supply chain and sales funnel, but can also result in legal ramifications. Non-compliance will result in fines of up to €15 million or 2.5% of global turnover and potential EU market bans, which could also result in a lack of brand awareness or worse, negative brand image.
Why the Automotive Industry Should Care
While most automotive vehicles are excluded from the CRA due to the overlapping nature of the CRA regulations with existing regulations (like the WP.29 R155 and EU General Safety Regulation, GSR), certain automotive components like digital components, aftermarket software, and connected services, as well as vehicles not covered under R155 (like construction or agricultural vehicles) are still subject to the CRA.
Vehicles are complex digital ecosystems, and with more and more technology being embedded into the architecture, compliance will also become more complex. While the details of the CRA are still being worked out, the automotive industry will have to move quickly, as the impacts of the regulation will be wide-ranging. Manufacturers and suppliers can begin by aligning with existing guidelines for cybersecurity resilience in vehicles:
• Standard and Regulation Compliance: Automotive manufacturers will have to ensure that they comply with the existing regulations like UNR-155 and GSR, and are recommended to follow standards like ISO/SAE 21434 when it comes to vehicle architecture and connected platforms.
• Secure OTA Updates: Manufacturers can ensure that their Over-the-Air (OTA) capabilities are secure and efficient, and ensure that vulnerabilities are patched in real-time.
• Regular testing: Testing current architecture for vulnerabilities can be a great starting point to analyze where mitigation is needed.
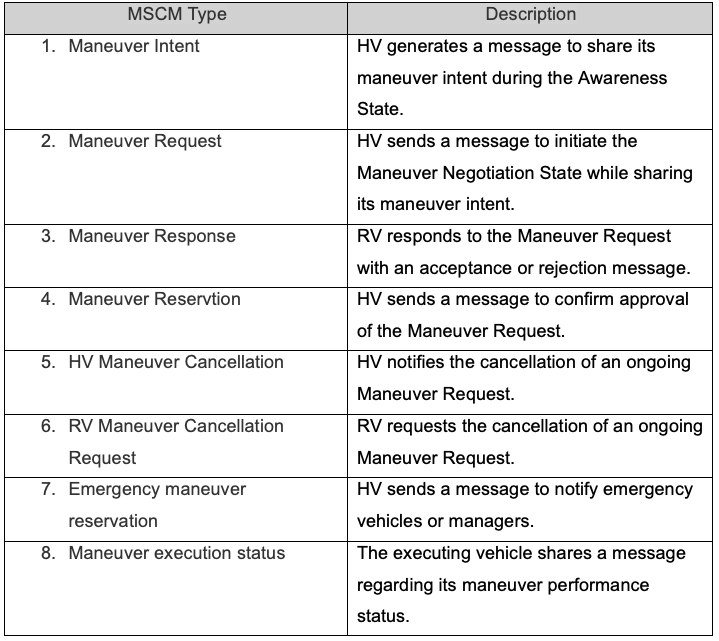
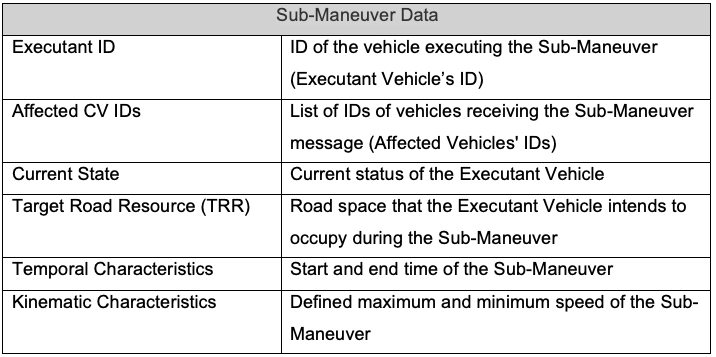
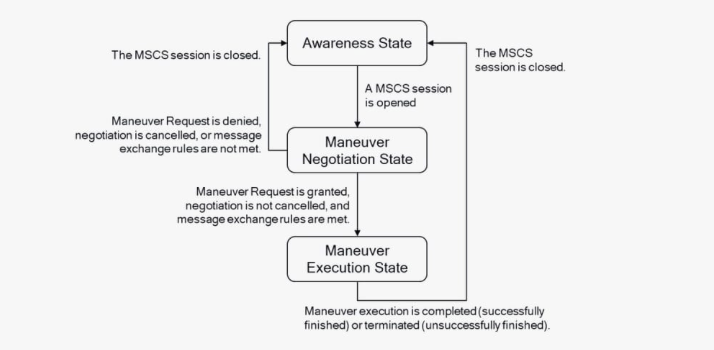
• V2X security and Security Credential Management Systems: While a Security Credential Management System (SCMS) isn’t explicitly required by the CRA, it can support compliance by demonstrating security best practices.
AUTOCRYPT has been closely involved in cybersecurity regulatory compliance from the early stages, focusing on practical, optimized solutions for manufacturers and suppliers. Our expertise in automotive and IT cybersecurity empowers our partners to seamlessly meet regulatory requirements while strengthening their product reliability, market competitiveness, and maintain a positive brand image.
To learn more about the CRA, click here. To contact our team about how your company can get started with CRA compliance, contact global@autocrypt.io.