Consulting Services
WP.29 Consulting
UNECE WP.29 regulations for automotive cybersecurity
The first-ever regulation requiring vehicle type approval with regards to cybersecurity. Are you prepared?
In June 2020, the United Nations officially adopted two new regulations regarding automotive cybersecurity. Set out by UNECE’s WP.29 working party, UN Regulation No. 155 mandates an automotive cybersecurity management system (CSMS), while UN Regulation No. 156 requires a software update management system (SUMS) for all vehicles. As mandatory prerequisites for vehicle type approval, the regulations affect the production of every vehicle across the globe.
Everyone needs to be prepared, from OEMs, Tier-1 suppliers, to software providers.
WP.29 is a ”Working Party on the Construction of Vehicles” established in 1952. It became officially known as WP.29 in March 2000 and the objective has always been to initiate and pursue actions for worldwide harmony in terms of the development of regulations for vehicles. The Working Party is the largest international vehicle regulatory system in the world.
While WP.29 has several working regulations for vehicles, the two regulations released in June 2020 are the first regulations that mandate cybersecurity measures and practices for vehicle development and production, hence impacting the entire automotive industry, signaling the growing importance of automotive cybersecurity.
Highlights
All You Need to Know About WP.29 Compliance
and stay prepared with AUTOCRYPT
Effects on the Automotive Industry
If the vehicle in question…
- Utilizes a wired or wireless connection to the vehicle’s internal communication network
- Utilizes a wired or wireless connection to the external communication network of the vehicle
- Connects indirectly to the vehicle network
- Utilizes electronic or optoelectronic hardware
- Includes software
- Includes sensors

WP.29 Regulation Checklist
While countries are beginning the steps towards full implementation, those in the automotive industry (including OEMs, Tier-1 Suppliers, service providers, etc.) can take it upon themselves to ensure they are prepared for WP.29’s stipulations.
UN R155: Cyber Security Management System (CSMS)
For Automotive Industry/Sector
- Identify and manage cybersecurity risks in vehicle design
- Verify that the risks are managed, including testing
- Ensure that risk assessments are kept current
- Monitor cyberattacks and effectively respond to them
- Support analysis of successful or attempted attacks
- Assess if cybersecurity measures remain effective for new threats and vulnerabilities
For Manufacturers
- CSMS is in place and its application to vehicles on the road is available
- Provide risk assessment analysis, identify what is critical
- Mitigation measures to reduce risks are identified
- Evidence that mitigation measures work as intended
- Ensure measures are in place to detect and prevent cyberattacks and support data forensics
- Monitor activities specific for the vehicle type
- Submit activity monitoring reports to relevant approval authority
UN R156: Software Update Management System (SUMS)
For Automotive Industry/Sector
- Record hardware/software versions for vehicle type
- Identify software relevant for type approval
- Verify software on components
- Identify interdependencies, especially with regards to software updates
- Identify vehicle targets and verify compatibility with update
- Assess if software update affects type approval or legally defined parameters (including adding/removing functions)
- Assess if an update affects safety or safe driving
- Inform vehicle owners of updates
For Manufacturers
- SUMS is in place and its application to vehicles on the road is available
- Provide SU delivery mechanism and ensure integrity and authenticity
- Protect software identification numbers
- Ensure that software identification number is readable from the vehicle
For Over-the-Air (OTA) Software Updates
- Restore function if update fails
- Execute update only if sufficient power
- Ensure safe execution
- Inform users about each update and about their completion
- Ensure vehicle can conduct updates
- Inform user when a mechanic is needed
AUTOCRYPT's Solution for WP.29
Many companies have already begun to map out a timeline implementing changes to their existing supply chains to ensure that new vehicle models will be compliant with the regulations. However, the comprehensive nature of the compliance regulations can prove to be roadblocks for many, requiring additional assistance.
As an automotive cybersecurity solutions provider, AUTOCRYPT offers a three-fold, comprehensive approach to CSMS compliance, beginning with consultation, all the way to regular testing.
Consulting and Training
AUTOCRYPT’s security professionals will work with you to conduct:
- Overview of existing CSMS
- TARA-based risk assessment
- Recommendations for security engineering
Testing
AUTOCRYPT provides a range of security testing tools and services:
- Vulnerability Scanning
- Fuzz Testing
- Penetration Testing
Embedded Security
AUTOCRYPT’s comprehensive In-Vehicle Systems security solution offers:
- Threat detection and monitoring
- Message encryption
- Security operation
Manufacturers, suppliers, and service providers should be looking to get a head start on structuring their Cyber Security Management Systems, and preparing for type approval. Ultimately, AUTOCRYPT and WP.29’s goals are one and the same: security should be a priority before any vehicles go on the road.
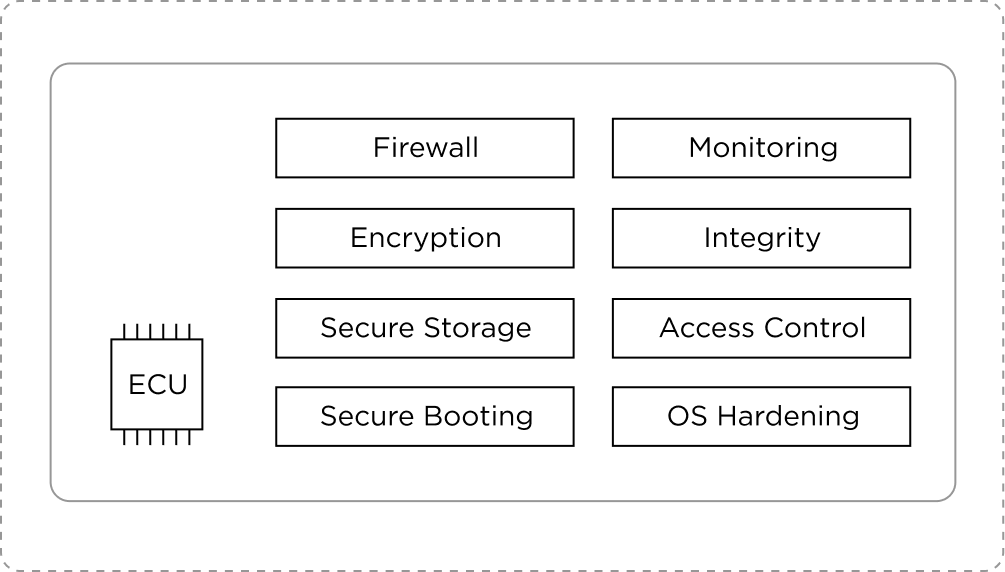
Security reinforcement and monitoring for ECUs
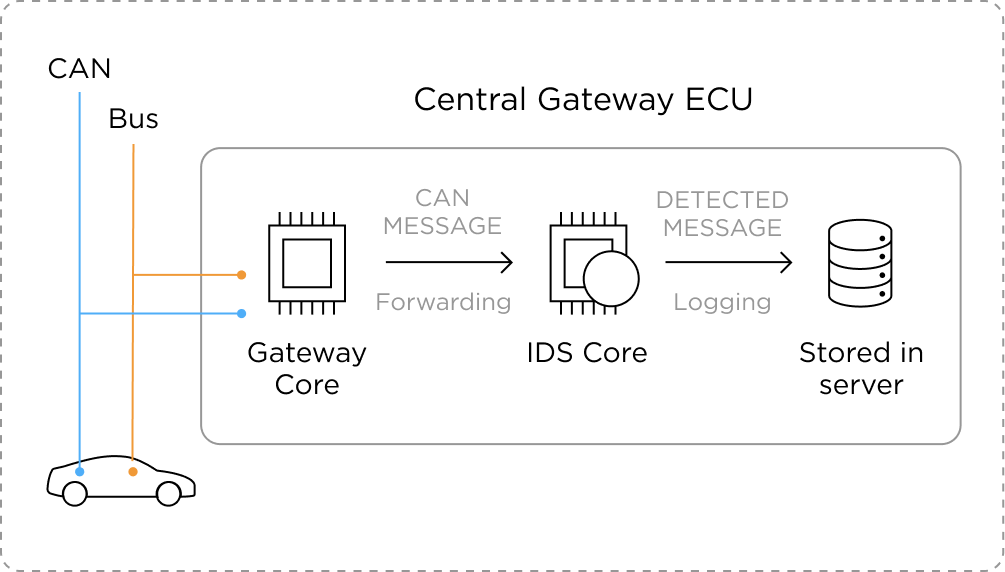
Abnormal behavior / attack detection for internal and external communication networks

Related Solution
In-Vehicle Security
AUTOCRYPT provides complete security for the internal systems of the car, monitoring all communications and responding to malicious activities.
About AUTOCRYPT
AUTOCRYPT
AUTOCRYPT is a mobility security provider with the goal of providing a seamless and secure mobility experience for all.

