In-Vehicle Systems
AutoCrypt Security Analyzer
Automated OSS vulnerability analysis and SBOM generation

Vulnerability-free vehicle software begins here.
As vehicles become increasingly software-defined, managing software vulnerabilities has become crucial to vehicle cybersecurity. Given that large parts of vehicle software are developed using open-source code, an effective vulnerability management solution is a must.
AutoCrypt® Security Analyzer (SA) detects and manages vulnerabilities in vehicular open-source software (OSS) by accurately identifying, categorizing, and listing its components in a software bill of materials (SBOM), implementable at all stages of the software development lifecycle (SDLC).
With Security Analyzer, OEMs are able to detect and eliminate OSS vulnerabilities in their vehicles starting from an early development stage, ensuring zero vulnerability in their vehicles prior to mass production.
Why Security Analyzer?
Addressing the Security Risk of Open-Source Software
Open-source software and open source code are dominating the software market. In the mobile OS market, over 70% of users worldwide use the Linux-based Android OS. A majority of operating systems hosting financial transactions are built from Linux and Unix. Over 99% of corporations worldwide utilize open-source code, with more than 70% of all software source code being open-source.
of all corporations use open-source software
0 %
of all software code is open-source
0 %
A software application tends to be built from different open-source components. It may contain lines of open-source code that are directly copied and pasted, somewhat modified, or form dependencies with other pieces of code within the software. This means that even if an OSS vulnerability is announced, developers may have a hard time figuring out whether their software contains components subject to that vulnerability. This puts many IoT devices, including vehicles, at risk.
Therefore, to manage OSS vulnerabilities, it is crucial to have a clear view of all open-source components and licenses within the software. The United States Department of Commerce has introduced the practice of the “Software Bill of Materials” (SBOM), which is a machine-readable inventory containing a list of ingredients that make up a piece of software, making it easy to detect, patch, and defend against OSS vulnerabilities.
How It Works
Vulnerability Analysis and SBOM Generation
AutoCrypt Security Analyzer is a solution that scans for vulnerabilities in vehicle software and derives an SBOM for continuous risk management.
1. Accumulates data
SA Vulnerability Database (VDB) stores and manages vulnerability lists provided by CVE, NVD, MITRE, and Bugzilla, along with machine learning-based patches, open-source components from software scans, and user-defined vulnerabilities.
2. Scans source code
SA Scanner scans a copy of the software’s source code, then stores it as an encrypted file (compatible with all programming languages).
3. Function-level analysis
By comparing the scanned source code (1) to the VDB (2), Security Analyzer performs vulnerability analysis based on both individual files and functions (via patented VUDDY® and CENTRIS® technology), capturing every dependency.
4. SBOM generation
Security Analyzer identifies and provides a list of all open-source components and licenses within the software (compatible with SPDX and CycloneDX formats), allowing for continuous vulnerability management.
5. Vulnerability management
After the analysis process, Security Analyzer provides a list of recommended patches for the discovered security risks, along with a detailed guide on the vulnerabilities so that users can manually fix coding flaws.
Multi-Factor Vulnerability Analysis
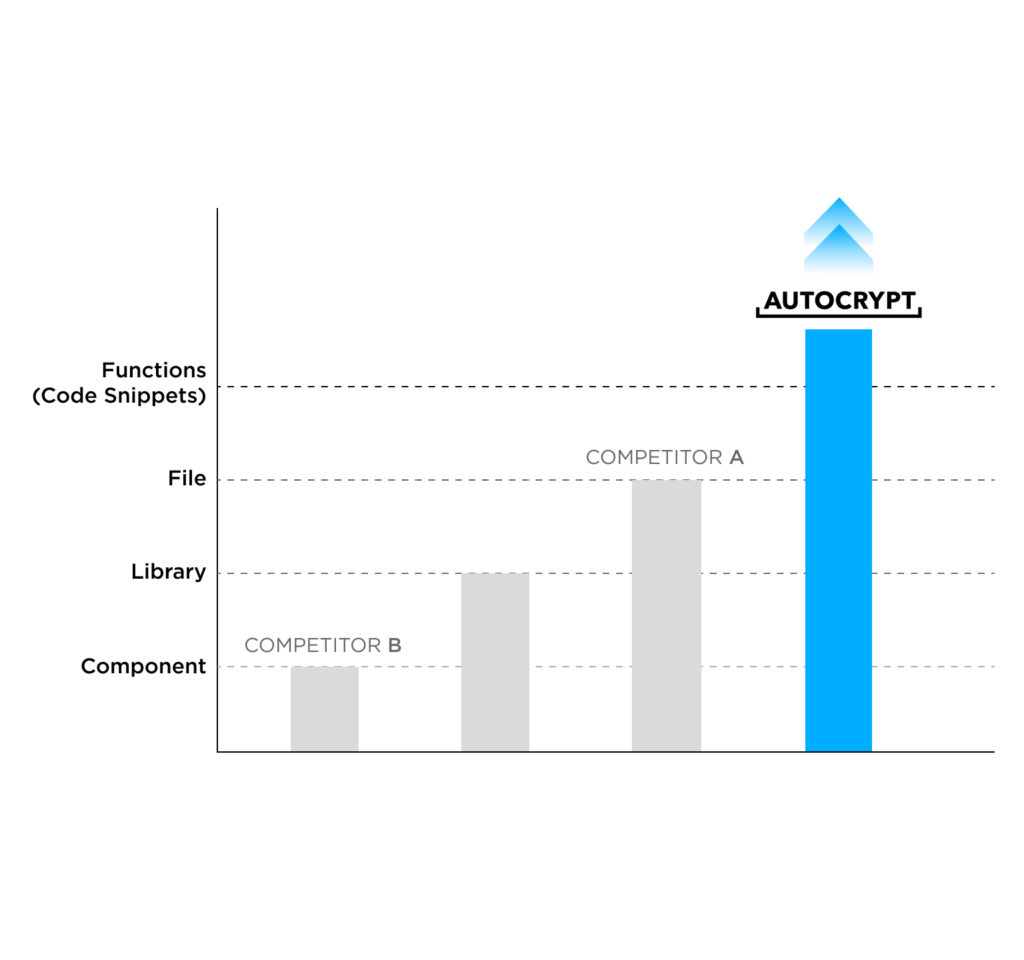
AutoCrypt® Security Analyzer runs a one-of-a-kind multi-factor vulnerability analysis using four different units of analysis: component, library, file, and function.
This contributes to exceptional accuracy in identifying all open-source components and licenses within the software.
Thanks to its patented function-level analysis, testing results at a third-party security research lab show that AutoCrypt® Security Analyzer has a significantly higher component identification rate and accuracy score compared to major competitors, accurately identifying 98% of all open-source software components.
Highlights

High Accuracy
Multi-factor vulnerability analysis ensures zero misdetection

Precise Patching
Backporting allows precise patching on only impacted components
Customizability
User can self-define vulnerabilities based on all four units of analysis
Zero-Day Protection
AI analysis helps detect and manage zero-day and unknown vulnerabilities

