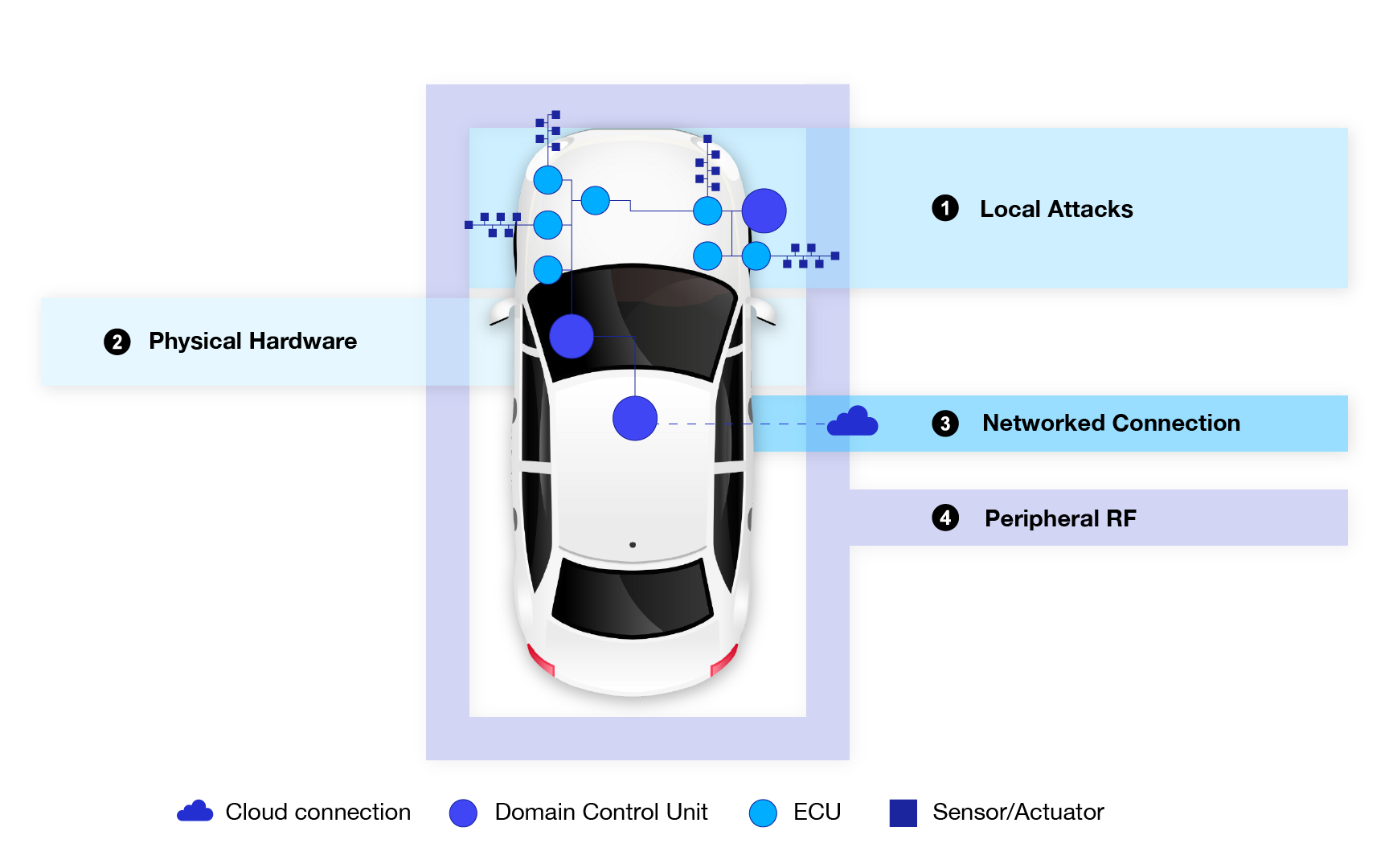
As vehicles continue to evolve into sophisticated, software-driven machines, automotive cybersecurity has become as critical as a car’s physical safety. Modern vehicles rely on millions of lines of code that must not only work seamlessly but also remain resilient to potential cyberattacks. Regulations and industry standards mandate manufacturers to safeguard their systems against these threats. Two fundamental processes in achieving this are security validation and vulnerability testing. While both aim to ensure software security, they take distinct approaches to achieve it. Let’s dive into their roles, differences, and why they’re indispensable for automotive cybersecurity.
Security Validation
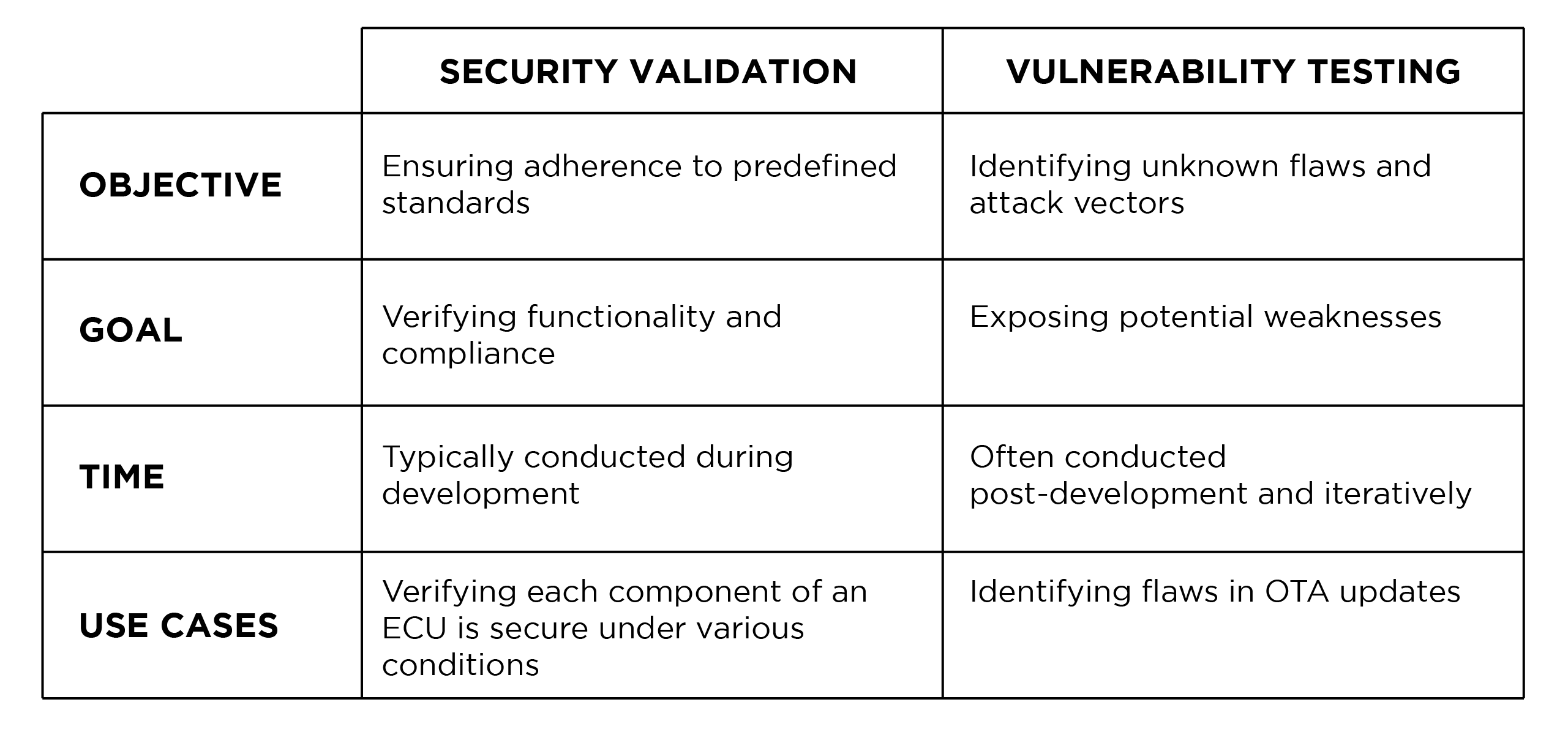
At its core, security validation is about ensuring that a system meets predefined security requirements and functions as expected under normal conditions. Think of it as a quality assurance process that confirms security measures are implemented correctly and comply with industry standards like UN R155/156 or ISO/SAE 21434.
For instance, security validation could involve verifying that Over-the-Air (OTA) update mechanisms comply with UN R156 requirements or ensuring that each ECU component is secure under different real-world conditions.
Manufacturers employ various testing methods to perform security validation, including but not limited to:
- Functional Testing, which ensures key features like encryption and authentication work correctly under normal use cases.
- Fuzz Testing, which introduces random or unexpected inputs to assess system stability and expose hidden vulnerabilities.
- Penetration Testing, which simulates attack scenarios to test the system’s ability to defend against real-world threats.
The primary goal of security validation is to provide confidence and documented proof that all cybersecurity measures are not only in place but also operating effectively according to regulatory standards.
Vulnerability Testing
While security validation checks compliance, vulnerability testing takes a broader approach, exploring potential weaknesses or flaws that attackers might exploit. This process identifies vulnerabilities—both known and unforeseen—through rigorous probing and stress testing. Given that vehicle software is constantly evolving, vulnerability testing must be an ongoing process to mitigate risks proactively.
Common techniques include:
- Fuzz Testing for Vulnerability Detection, which detects weaknesses by feeding unexpected or malformed data into the system.
- Network and Protocol Testing, which analyzes communication protocols such as CAN, LIN, and Ethernet for exploitable flaws like injection vulnerabilities.
- Hardware Security Testing, which examines hardware-software interactions, such as the extraction of firmware from electronic control units (ECUs), for potential vulnerabilities.
Unlike security validation, which confirms what is known, vulnerability testing ventures into the unknown, uncovering potential attack vectors that may not have been anticipated during the development process.
Key Differences Between Security Validation and Vulnerability Testing
By combining these two processes, manufacturers can build automotive systems that are not only compliant but also resilient to cyber threats.
As the automotive industry moves toward greater connectivity, the stakes for cybersecurity are higher than ever. Security validation ensures that systems meet regulatory standards, while vulnerability testing helps uncover hidden risks before malicious actors can exploit them. Together, they form a comprehensive approach to protecting vehicle systems from cyber threats.
For instance, validating the proper encryption of V2X communication provides compliance, but only through vulnerability testing can potential flaws in cryptographic implementation be identified. By integrating both practices into the development lifecycle, manufacturers can ensure their systems are secure and future-ready.
Cybersecurity in modern vehicles is no longer an optional feature—it’s a foundational requirement. Security validation and vulnerability testing are two sides of the same coin, each addressing distinct yet complementary aspects of the security landscape. When combined, they provide the robust framework needed to protect vehicles from both known and emerging cyber threats.
For manufacturers, embracing these processes is not just about meeting regulatory requirements—it’s about staying ahead in an industry where safety, innovation, and trust go hand in hand.
To learn more about AUTOCRYPT’s vehicle cybersecurity testing measures and cybersecurity regulation compliance consulting services, contact global@autocrypt.io.