It has long been established that cybersecurity is becoming more important in the automotive industry. The mass adoption of cybersecurity practices in the industry is in line with the development of vehicle technology. Nowadays vehicles have more complex internal structures and are more exposed to external communication channels, meaning that there are more endpoints that need protection from cyber threats. Automakers are turning to various cybersecurity approaches to secure their vehicles, one of the most common ones being automotive intrusion detection systems (IDS).
What is an Automotive IDS?
An automotive IDS is an intrusion detection system adapted specifically for the automotive industry. These solutions monitor network traffic entering and traversing the vehicle, as well as the activities within the vehicle’s components, to detect traffic anomalies or potentially malicious activity. IDS compares the monitored traffic and behaviors against a database of known cyber threats and attack patterns. If a match is found, it raises an alert to the relevant administrators or security personnel to address.
Automotive IDSs typically employ two main detection methods:
1. Signature-based detection: Matches observed activity against a database of known malicious patterns or signatures.
2. Anomaly-based detection: Identifies deviations from established normal network behavior or activity baselines, flagging any unusual activities that might indicate a potential intrusion.
It’s important to note that an intrusion detection system is a monitoring tool, meaning it detects threats but does not actively prevent or mitigate them. Upon detecting anomalous behavior or a potential threat, the IDS sends an alert, allowing administrators to investigate and take appropriate action.
Types of Automotive IDS
IDSs are categorized based on their deployment location and the scope of activity they monitor. In the automotive context, we will discuss two main types:
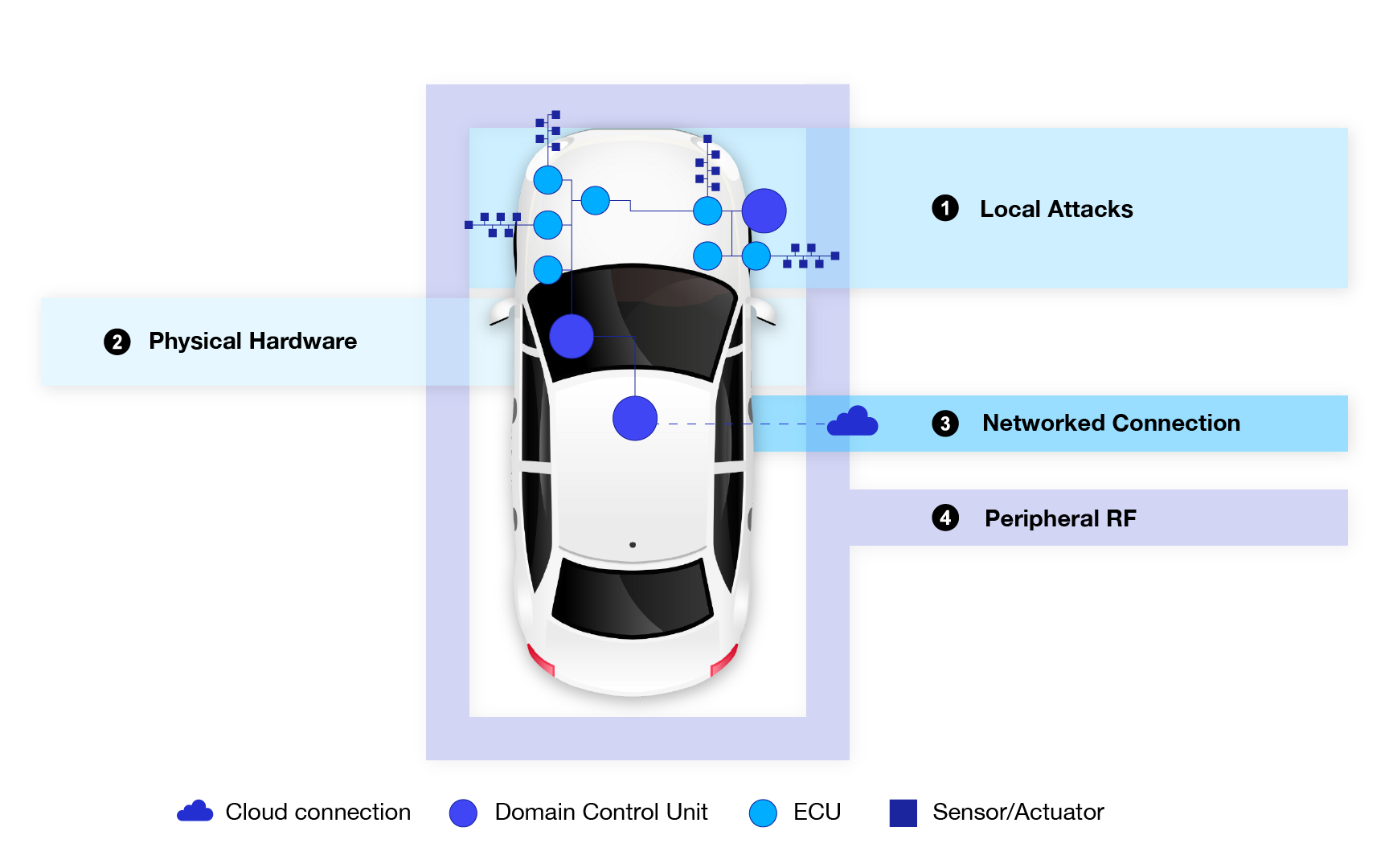
1. Network-based IDS (N-IDS)
A network-based IDS monitors the entire vehicle network for anomalous activity, checking all incoming and outgoing traffic. This provides a broad, network-level view of potential threats and can detect attacks targeting the vehicle’s communication channels or network infrastructure.
2. Host-based IDS (H-IDS)
A host-based IDS is a security software designed to monitor the activities of an individual host or vehicle component, such as an Electronic Control Unit (ECU). It focuses on detecting threats targeting specific systems or components within the vehicle, providing a more granular level of cybersecurity monitoring.
While implementing either one of these intrusion detection system types will help protect an automobile from cyber attacks, most contemporary vehicles will benefit from a mix of both host-based and network-based IDS. For instance, Autocrypt’s IDS combines both network-based and host-based IDS to ensure maximum threat monitoring coverage across the vehicle’s network and individual components.
Comprehensive Vehicle Protection
To ensure comprehensive vehicle protection, automakers are highly advised to implement multiple cybersecurity solutions simultaneously. Since an IDS is a monitoring-only device, pairing it with an Intrusion Prevention System (IPS) would ensure that malicious activities are not only detected but also mitigated.
Additionally, implementing diverse cybersecurity measures will help automakers better address the requirements of vehicle cybersecurity regulations like UN R155 and R156, which mandate cybersecurity throughout the entire vehicle lifecycle.
By adopting a multi-layered approach with complementary cybersecurity solutions like IDS, IPS, and others, automakers can significantly enhance the overall security posture of their vehicles, safeguarding them against a wide range of cyber threats in today’s connected automotive landscape.
Visit our in-vehicle security solutions page to find the solution that best fits your cybersecurity needs.
Follow AUTOCRYPT on LinkedIn to stay informed about our latest news and blogs.