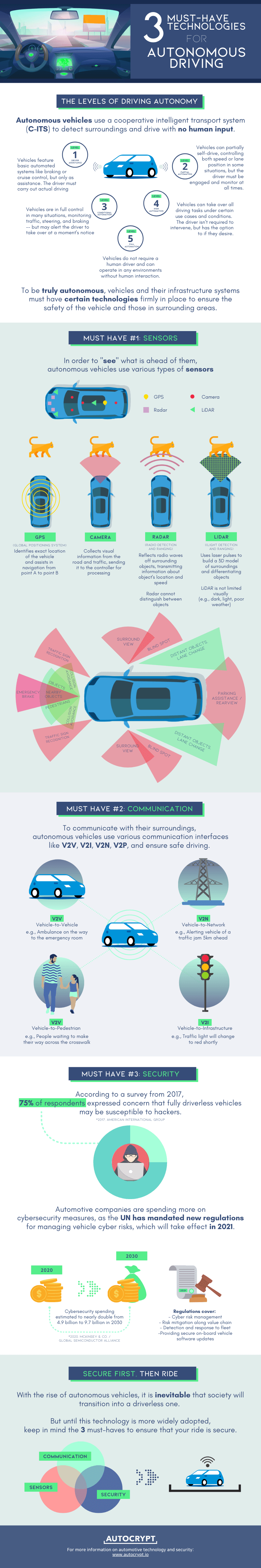
Modern vehicles have a lot of advanced safety features that keep us safe on the roads. Blindspot detection, lane keep assist, and forward-collision assist with automatic emergency braking (AEB) are some of the standard features that we take for granted. Moving a bit upward, a typical high-end vehicle today has face detection capabilities that would send all kinds of warnings when it sees the driver drowsing. If the driver fails to wake up, the car would slowly park itself on the roadside.
Very soon in the future, we are likely to see a significant decrease in traffic accidents when older cars get phased out. However, not everything is as rosy as it seems. Modern cars are essentially sophisticated computers on wheels. The more sophisticated they are, the more weak points they have, and the more possibilities for high-tech attackers to exploit them.
Indeed, modern cars are keeping us safe. But who keeps cars safe? (Hint: AUTOCRYPT)
We need to understand where the threats come from and take the correct measures to prevent them. Here we take a look at six of the top security threats for connected vehicles.
1. Attack on Smart or Digital Keys
Smart keys commonly referred to as “keyless entry”, do not require the driver to push any buttons on the key to unlocking the doors. Doors unlock automatically when the key fob is near the car. Smart keys mostly utilize infrared radiation (IR) technologies to transmit signals to the car. Digital keys built-in mobile applications work in a similar way, except that they transmit signals via Bluetooth or NFC technologies.
Under situations where the key is nearby a locked vehicle, a hacker could break into the car by gaining access to the IR communication with a brute-force attack, by using a relay box to scan and reflect the communication signals, or by manipulating the Bluetooth communication between the smartphone and the vehicle. Automakers have started to make keys with much shorter signal transmission ranges, in which the key fob or smartphone needs to be right beside the doors for them to unlock.
2. Attack on Embedded Software
Modern cars have up to 80 electronic control units (ECUs) that keep the vehicle functioning. The embedded software in these ECUs is not only growing in numbers but is becoming increasingly complex. Critical functions like the anti-lock braking system (ABS) and electronic injection lineup are all controlled by ECUs. The embedded software analyzes data such as temperature, engine speed, and accelerator position to determine the optimal behavior of the fuel injectors, hence delivering the optimal results depending on the driver’s settings (e.g. eco, comfort, sports, etc.).
Attackers can inject malware into the ECUs to manipulate their state and actions, posing a significant threat on the functioning of the vehicle. To protect these built-in software from external threats, automakers need to provide prompt software patches and invest in a reliable in-vehicle firewall.
AutoCrypt IVS is an advanced firewall optimized for automotive communication protocols. With two decades of experience in intrusion detection, AutoCrypt IVS effectively blocks all malicious traffic from entering the vehicle system. Click here to learn more.
3. Attack on Software Applications
In-vehicle infotainment systems have become just as important as the engines. Other than the built-in applications, Android Auto and Apple Carplay are now offering an increased number of vehicle-compatible mobile applications from a wide range of categories, including navigation apps, payment apps, media apps, social networking apps.
Similar to embedded software, built-in software applications need to be constantly updated and patched, as well as protected by an in-vehicle firewall. To prevent threats coming from mobile applications, vehicle-to-device (V2D) security measures should also be deployed.
AutoCrypt V2D is a security solution that protects the communications between vehicles, mobile devices, and cloud service providers. Click here to learn more.
4. Attack on Sensors
The majority of modern cars have certain degrees of autonomous driving capability, ranging from SAE Level 1 to Level 4. (Click here to see SAE’s automation level definitions.) To provide such driving assistance and autonomous driving features, a wide range of sensors must be built within the cars to help them detect road conditions, lighting conditions, obstacles, moving objects (e.g. cars and pedestrians), and inertia. Cars also rely on GPS data to locate and navigate with high precision.
Threat actors could exploit vulnerabilities in these sensors to undermine their range, detection capabilities, and reliability. They could also manipulate GPS data to provide wrong directions and control the route of the vehicle (for Level 4 automation). State-backed APT groups could hack into the sensors of multiple vehicles to cause mass-scale collisions and destruction.
5. Attack on Cloud-based Servers
After the sensors collect all the data, they transmit that information to the cloud database to enhance the autonomous driving experience, and also to enable communications between the vehicle and the transportation system. Thus large amounts of data are sent to the cloud database.
Sophisticated threat actors could compromise the cloud databases to steal sensitive information about the vehicles and the drivers. These data could be used to identify weaknesses of a vehicle, which could be exploited for future intrusions and phishing campaigns.
6. Attack on Networks
Modern vehicles are all part of the vehicle-to-everything (V2X) network. The V2X network consists of countless numbers of vehicle-to-device (V2D), vehicle-to-grid (V2G), and vehicle-to-infrastructure (V2I) communication messages. These communications would increase substantially once cooperative-intelligent transportation systems (C-ITS) roll out on a large scale. As such, a car is exposed to hundreds of endpoints that could serve as entry points for hackers.
To protect the car in a V2X network, an in-vehicle firewall is not enough. An authentication framework must be put in place to verify every user before allowing them to connect to the vehicle system.
AutoCrypt V2X utilizes user authentication and data encryption technologies to secure all sensitive information related to the vehicle. AutoCrypt PKI supplements V2X by offering a certificate-based authentication system for external users like vehicles, pedestrians, and road infrastructure. Click here to learn more.
Safety is the Number One Priority
Safety has always been paramount in transportation. We expect seatbelts and airbags to work in the event of a collision, and expect the car to not catch on fire after crashing. But as we transition into this new era of connected vehicles, we as consumers do not seem to have any clear expectations yet.
This is why AUTOCRYPT is not only providing the most complete vehicle security solution for the industry. It is also working with automakers and other security experts to establish an international security standard that would help shape expectations, set up high standards, and keep our roads safe in the era of automation.