In recent years, the automotive industry has been abuzz with the term “software-defined vehicle” (SDV). With an increasing number of original equipment manufacturers (OEMs) claiming to be at the forefront of SDV development, it’s essential to understand what truly makes a vehicle software-defined. In this blog post, we will delve into the concept of SDVs, their current state of development, and the industry trajectory for the future.
The Ultimate SDV: What Does It Entail?
Before we dive into the ultimate vision for SDVs, it’s crucial to recognize that modern vehicles already incorporate various software-defined features like in-vehicle infotainment, driver assistance systems, and cellular connectivity technologies. These features are adding advanced capabilities to our vehicles, digitizing the way we interact with our cars and improving the driving experience. However, they do not represent the final destination of SDV technology.
The ultimate SDV is a vehicle that has undergone a profound transformation in its design and functionality. It is not just about adding software-enabled features, it’s about making software the central nervous system of the vehicle.
An SDV’s value lies primarily in the software that enables advanced capabilities like cloud connectivity and autonomous driving. And while the hardware is still important, software will be the differentiating factor in new generation SDVs. Software maintenance and upgrading will be the most economical, convenient, and efficient way for future OEMs to provide a differentiated product and improve customer satisfaction. OEMs are spending countless resources on R&D to make this possible.
The ultimate software-defined vehicle is a supercomputer vehicle that supports increased flexibility, customization, and remote upgradeability of functionalities.
A crucial element that enables this level of flexibility in SDVs is cloud connectivity which powers over-the-air (OTA) software downloads and updates. Vehicle-cloud connectivity has the potential to significantly cut back costs for new software rollouts, as new functionalities can be introduced over-the-air without the need to alter underlying hardware.
Besides development cost savings, OTA software implementation can create monetary value in the face of software subscription models for OEMs. We have already seen this phenomenon rise in the industry with the likes of Tesla offering subscription-based functionalities, like full self-driving, to its customers.
The goal of the industry is to reach a point where vehicle software and hardware development can be done independently from each other. This will require the entire industry to embrace innovation and shift away from the traditional vehicle manufacturing process.
Necessary Technology for SDVs
Emphasizing the role of software in a vehicle will require separating vehicle software from its hardware. Achieving complete software and hardware decoupling requires a fundamental shift in vehicle architecture and supply chain operations.
Traditionally, Tier 2 electronic control unit (ECU) manufacturers embed software within the hardware. This limits OEMs from implementing software changes down the road. The decoupling of software from hardware would allow the vehicle software to operate independently, similar to a smartphone. Applications can be downloaded from the app store and updated OTA.
In addition, complete software-hardware decoupling has the potential to significantly accelerate software development times. This enables scaled and continuous software improvement across a vehicle’s serviceable life, all while incurring lower development costs.
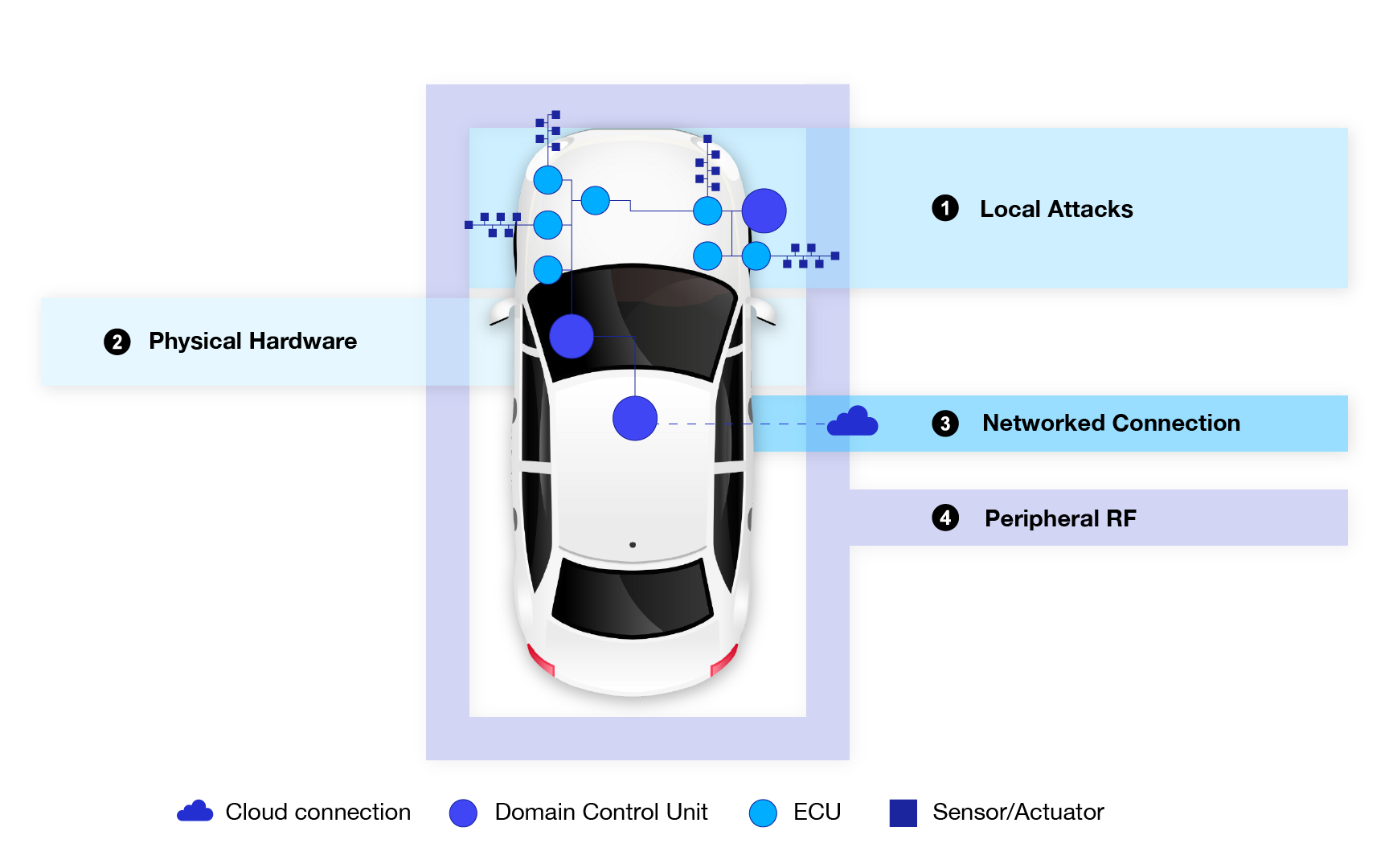
Reaching decoupling will take a complete reshuffling of the current distributed electrical/electronic (E/E) vehicle architecture into a centralized system defined by a central computing unit. This cardinal change is needed due to the fact that a distributed vehicle architecture cannot keep up with the increasingly higher computing power needed for SDVs. On the other hand, if a car has 100 ECUs, all of these ECUs would have different embedded software that could be based on completely different platforms. This makes software implementation very difficult, if not impossible.
Centralizing vehicle electronics simplifies management and allows for more efficient software integration. The development of a centralized architecture would allow OEMs to implement software updates directly to the central processing unit, which is exponentially more time and cost-efficient. It will also encourage OEMs to utilize standardized or open-source software platforms for SDVs. This shift will allow for higher system integration within the vehicle and functions like high-speed connectivity to the cloud, other vehicles, and smart infrastructure.
Moreover, open-source software is gaining traction in the automotive sector. Open-source software platforms provide a collaborative environment for developers to contribute to SDV technology, accelerating innovation.
Current State and Future Trajectory
The entire automotive industry is currently in the midst of the transformation towards software-defined vehicles. Normally, Tier 2 component suppliers, who are in charge of embedding software within their chips, do not have direct contact with OEMs and have to go through Tier 1 suppliers. However, nowadays we are witnessing a seismic shift in supply chain operations signified by a demand for software suppliers. Tier 2 and pure-play software developers are gaining a stronger position within the supply chain, indicating a shift towards prioritizing software expertise. As the automotive industry is going through a technological shakeout, the supply chain is also turning more horizontal, allowing for less restricted relations between supply chain participants.
Furthermore, there is a rising trend of industry collaboration as automakers realize the complexity and scale of SDV development. We have seen some of the largest traditional OEMs welcome partnerships with technological companies. Stark examples are partnerships between Qualcomm and Mercedes-Benz, BMW and Amazon, BYD and Baidu, where automakers are turning to tech companies to spearhead SDV development.
Cross-industry partnership is showing that the automotive sector is ready to stir away from tradition in the name of innovation.
Regulations and Standards
As the SDV landscape evolves faster than ever, regulations and standards play a crucial role in ensuring vehicle safety and security. The United Nations UNECE WP.29 set out two regulations for vehicle type approval. UN R155 addresses vehicle type approval with a focus on cybersecurity and cybersecurity management systems, and UN R156 mandates secure software updates and implementation of software update management systems.
These regulations enforce software-defined vehicle development that is secure by design. UN R155 mandates that cybersecurity principles are implemented at the core of business processes, vehicle architecture design, risk assessment, and security control implementation. This means that cybersecurity regulations are implemented throughout the entire supply chain.
While these regulations are legally binding for the countries that have signed the agreement, ISO/SAE 21434 serves as an international standard for road vehicle cybersecurity engineering. Companies may choose to adhere to this standard voluntarily.
Enabling SDVs is more than just creating advanced software for vehicles. SDVs must be designed with cybersecurity as a core element. Regulations and standards ensure safe and standardized SDV development.
The concept of software-defined vehicles represents a transformative shift in the automotive industry. The ultimate SDV envisions complete software and hardware decoupling, cloud-based software, and a smart, connected driving experience. With the industry’s current trajectory towards SDV development, coupled with evolving regulations, we are witnessing the dawn of a new era in mobility where software takes the driver’s seat.
AUTOCRYPT secures the rapidly evolving mobility space with in-vehicle cybersecurity solutions developed according to WP29 and ISO standards. Backed by decades of expertise in automotive cybersecurity we ensure a safe transition to software-defined vehicles.
To learn more about our services and solutions contact global@autocrypt.io.