We all know that vehicle-to-everything (V2X) communication constitutes the core of autonomous driving. By enabling vehicles and infrastructure to share live information, a safe and seamless autonomous mobility experience can be accomplished. But how exactly does the information sharing process work?
Just like how we communicate with each other via text messages, vehicles communicate with nearby entities by transmitting basic safety messages (BSM) between one another. However, different from us sending text messages, vehicles can send, receive, and process thousands of messages per minute. Every BSM a vehicle sends out contains the current time, along with the vehicle’s speed, location, direction, path, and other safety-related information. The vehicle that receives the BSM will use such information to determine whether it should change its speed and direction, or simply just send an alert to the driver. Despite seeming like a lot of work, this process is totally seamless, where hundreds of BSMs are sent, received, processed, and acted upon within each second.
Sounds easy? While the concept of V2X communication may seem very straightforward, we must figure out how to keep these communications perfectly accurate and effective. A failed, inaccurate, or miscommunicated text message is not usually a great deal. But a failed BSM is a matter of life and death. In fact, it would be fair to say that only 10% of the V2X communication technology is about communication itself, while the rest 90% is about ensuring that these communications are flawless and secure.
The Role of the Security Credential Management System (SCMS)
The Security Credential Management System (SCMS) is a proof-of-concept (POC) security solution for V2X communication. Despite the fancy name, it is essentially a public key infrastructure (PKI) designed to secure V2X messages – in this case – the BSMs. The POC has been officially adopted as a protocol by the United States Department of Transportation (USDOT) and became an industry standard for all providers of PKI-based V2X security solutions, including AUTOCRYPT.
Just like typical PKIs, the main purpose of the SCMS is to ensure trusted communication by securing the message. This involves a three-step process: certificate issuance, encryption, and certificate-based authentication. In simple terms, the SCMS needs to first ensure that the message sender is a legally registered entity, then encrypt the drafted message, after which from the receiver’s side, it needs to ensure that the message is truly the original message and that it has not been altered during transmission. Nevertheless, there are still two major differences between the SCMS and traditional PKIs.
The first difference is capacity. A single SCMS can issue up to 300 billion certificates per year, enough to support up to 300 million vehicles. On the other hand, the largest PKI to date is the Europay-Mastercard-Visa Consortium (EMVCo), which is only capable of issuing less than 10 billion certificates per year.
The second difference is that the SCMS faces a much more demanding situation. PKIs used for financial transactions have one sole purpose of ensuring security. Yet, the SCMS must excel in both security and efficiency, two attributes that are usually viewed as tradeoffs.
How Does the SCMS Work?
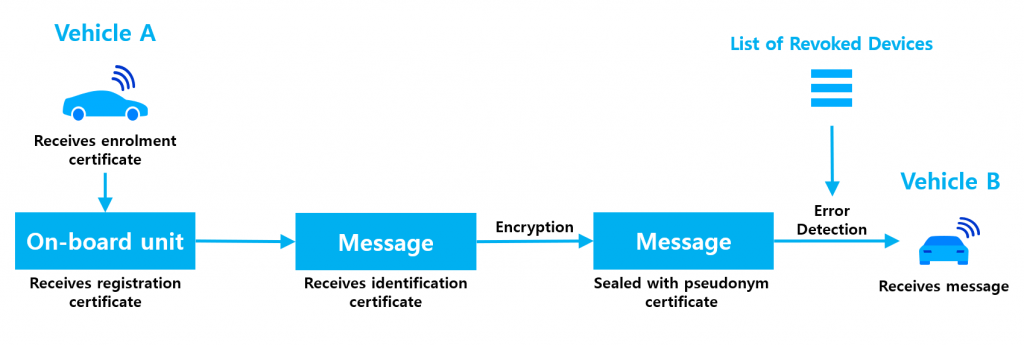
When a connected vehicle wants to join the V2X network, it must first send its registration request to the SCMS. After approving the request, the SCMS issues an enrolment certificate to the vehicle. The enrolment certificate acts as the ID for the vehicle, proving itself as an authorized participant.
Now that the vehicle is enrolled to send and receive messages. The SCMS still faces the task of securing the message. In this process, it needs to issue and manage several authorization certificates. Before sending out a message, the on-board unit (OBU) must receive an identification certificate. This certificate acts as a digital signature that gets attached to the message. To protect the privacy of the driver, the identification certificate is encrypted and turned into a pseudonym certificate that does not reveal the identity of the vehicle owner.
Before the receiver opens the message, the SCMS compares the sender’s digital signature with a list of previously revoked signatures to ensure that the signature is currently valid. After passing all verifications, the message is given to the receiver to process.
Other entities like roadside infrastructure also undergo the same process before sending a message. Roadside units (RSU) receive application certificates that are equivalent to the identification certificates of OBUs. However, in this case, there is no need to transform them into pseudonym certificates.
Why is the SCMS Useful for V2X Security?
Ensuring data integrity. In the V2X communication process, it is crucial to ensure that the message transmitted is not altered by any third party. Since the SCMS seals the messages with digital signatures, then verifies the signature upon receival. There is no endpoint for malicious actors to manipulate the message.
Ensuring data authenticity. Since an identity certificate is issued every time before a sender sends a message, there is no potential loophole for a threat actor to send fake messages in the identity of someone else.
Ensuring privacy. As mentioned above, the identity certificate issued to an OBU is encrypted into a pseudonym certificate. On top of that, the message itself only contains information on the vehicle’s condition and behaviour but not the vehicle’s identity. This makes it nearly impossible to trace the message back to the sender vehicle’s owner.
Ensuring interoperability. Instead of having V2X security providers developing their own set of mechanisms, the SCMS acts as a protocol that ensures all the developed solutions are interoperable with one another. This is a key benefit because interoperability is crucial to V2X communication.
Revocation. Different from traditional PKIs, the SCMS keeps a record of all revoked devices that had been reported with misbehaving, malfunctioning, or even malicious actions. The record helps prevent the same threats from reoccurring, significantly lowering the risks associated with the system.
AutoCrypt V2X, Securing Autonomous Driving with Decades of Experience in PKI
The SCMS protocol is complemented by a few other industry standards to ensure the deployment of secure and efficient PKIs for the V2X network. As such, AutoCrypt PKI is not only designed based on the SCMS, but also is in line with the Crash Avoidance Metrics Partners (CAMP) and the Cooperative ITS Credential Management System (CCMS). Combining AutoCrypt PKI with the software development kit installed locally into the OBUs, along with AutoCrypt LCM, the local certificate manager in charge of message encryption, AutoCrypt V2X is the most complete solution for autonomous driving.
To keep informed with the latest news on mobility tech and automotive cybersecurity, subscribe to AUTOCRYPT’s monthly newsletter.